The public cloud is a predominantly Software-as-a-Service (SaaS) market, with the Infrastructure-as-a-Service (IaaS) and Platform-as-a-Service (PaaS) elements gaining steadily in SaaS' rear view.
Oh, and that SaaS market is still wide-open, even as the IaaS/PaaS sector becomes more consolidated by the year.
Those are the main takeaways of IDC's useful snapshot of public cloud revenues, released Tuesday. The numbers come in a 2019 after-action report showing combined public cloud revenues of $233.4 billion, SaaS revenues of $148.5 billion, IaaS revenues of $49 billion and PaaS revenues of $35.9 billion. Significantly, all of this data predates the effects of the global pandemic.
Specifically, SaaS makes up nearly two-thirds of the public cloud market (64 percent). The sector's growth is still half that of IaaS and PaaS, making it a long slog for those two to catch up. SaaS had 2019 year-over-year growth of 20 percent, while IaaS and PaaS were both near 39 percent. Meanwhile, SaaS application growth has been slowing slightly in recent years, although the current crisis could reverse that trend.
IDC has started looking broadly at the public cloud market as two main buckets, rather than three. There's SaaS on the one side and IaaS and PaaS together on the other side. The market research company explains the grouping as reflecting the way end customers consume the services when deploying applications on the public cloud.
When it comes to market consolidation, those two buckets tell very different stories.
 [Click on image for larger view.] Source: IDC
[Click on image for larger view.] Source: IDC
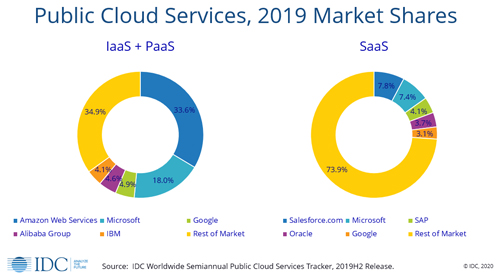
While SaaS is more mature from a revenue and growth perspective, the market is completely disorganized, owing partly to the nearly infinite variety of applications involved. Market leader Salesforce.com commands only 7.8 percent of total revenues. Microsoft, with its many SaaS offerings headlined by Office 365 and Dynamics 365, is second with 7.4 percent. After a top five rounded out by SAP, Oracle and Google, the "rest of market category" accounted for a whopping 74 percent of revenues in 2019.
On the IaaS + PaaS side, it's a highly consolidated market, with Amazon in the lead at 34 percent, Microsoft next at 18 percentand Google, Alibaba Group and IBM all in a tight market share range between 4 percent and 5 percent. The entire rest of the market in 2019 took 35 percent of the revenue, IDC said.
Still, IDC, which spends much of its time characterizing market sectors, viewed the rest of the IaaS/PaaS market as healthy. AWS and Microsoft have more than half of global revenues, but the firm sees a vibrant market of companies with what it describes as targeted use case-specific PaaS offerings.
IDC cautioned that next year's snapshot of the 2020 public cloud may show very different results from the trends suggested by the 2019 numbers, especially because of an acceleration in enterprises' shift to the cloud.
Posted by Scott Bekker on August 18, 20200 comments
Microsoft revenues were up 13% in the fourth quarter as the company continued its growth amid the pandemic and associated economic headwinds.
Revenues for the quarter, ended June 30, hit $38 billion. Diluted earnings per share decreased 15%, to $1.46, in part because the company took a $450 million charge in the quarter for its late-June move to permanently shutter the Microsoft Store physical locations.
Microsoft's stock price was down about 3% in after-hours trading, even though both the revenues and earnings announced Wednesday beat analyst expectations.
"Our commercial cloud surpassed $50 billion in annual revenue for the first time this year. And this quarter our Commercial bookings were better than expected, growing 12% year-over-year," Microsoft CFO Amy Hood said in a statement.
For the full year, revenue grew 14% to $143 billion and diluted earnings per share were also up 14% to $5.76.
Despite the cloud growth, investors may have been concerned about the sequential drop in Azure growth. While Microsoft does not break out Azure revenues, the company reports percentage growth. In the third quarter, Azure growth had been 59%, while the fourth quarter brought 47% growth.
By major business units for the quarter, Productivity and Business Process was up 6% to $11.8 billion, Intelligent Cloud was up 17% to $13.4 billion and More Personal Computing was up 14% to $12.9 billion.
Other notable growth trends in Microsoft's business-oriented product lines included:
- A 19% jump in Office 365 Commercial revenues
- Growth of 38% for Dynamics 365 revenue
- An increase of 19% in server products and cloud services revenue, which included the 47% Azure revenue growth
- Growth of 7% in Windows OEM revenue
- A 28% hike in Surface revenues
Posted by Scott Bekker on July 22, 20200 comments
Satya Nadella has been shopping around the term "tech intensity" for a year-and-a-half as a sort of refinement of, or at least a related concept to, "digital transformation."
But at the Microsoft Inspire partner conference on Wednesday, the Microsoft CEO elevated "tech intensity" to an organizing principle that can help companies both weather the current historic global challenges and perhaps grow after those challenges have started to recede.
"While the pandemic has taught us that no business is 100 percent resilient, those fortified by digital technology are more resilient, more capable of transforming when faced with these secular structural changes in the marketplace. We call this tech intensity, and every organization and every industry will increasingly need to embrace it in order to be successful and grow," Nadella said during his keynote at the two-day virtual event that wrapped up Wednesday (emphasis added).
Nadella said Microsoft is working with the Harvard Business School to develop frameworks and scorecards for companies in various verticals related to tech intensity.
"Tech intensity inside of an organization creates new operating architecture, breaking up the traditional silos to expose the technology and data and business process workflows inside the company in a very modular platform. This enables citizen developers, in collaboration with their digital and IT teams, to respond to these changes in the marketplace, this new opportunity, with agility. Our collective opportunity is to channel this intelligent cloud and the intelligent edge era into tech intensity for every business on the planet," Nadella said.
In the lead-up to his tech intensity definition, Nadella worked through a several verticals where customers and partners are exhibiting tech intensity.
They included:
- Health care and the surge in telehealth: "More than half of the primary care visits at some of the major health care systems are now being conducted virtually, and providers are increasingly relying on new capabilities like these AI-assisted bots to ensure patients get the information they need whenever and wherever they need it."
- E-commerce: "[It] has been pulled forward multiple years, according to one analyst. Offline retailers are embracing new models like contactless shopping, curbside pickup."
- Financial tech: "People [are putting] aside their physical wallets in favor of digital ones, and banks are harnessing the power of AI to manage risk."
- Manufacturing: "Every category [is] moving to automate everywhere, simulate anything and quickly advancing from early experiments with IoT and AI to rapid adoption at scale, creating digital twins and using mixed reality for remote assistance and field service."
 [Click on image for larger view.]
[Click on image for larger view.]
Fitting the effort to Microsoft's product set, Nadella emphasized a hierarchy with Azure at the foundation, GitHub and Power Platform in a middle development layer, and Microsoft 365 and Dynamics 365 on top. Enhancing the three clouds and development tools were Microsoft's security, compliance and identity tools.
Posted by Scott Bekker on July 22, 20200 comments
In the opening sessions of the Microsoft Inspire partner conference Tuesday, Microsoft executives urged partners to pivot their efforts to remote work, business continuity, security and cloud migration over the next year in a work world that the pandemic has "changed forever."
Gavriella Schuster, Microsoft's worldwide channel chief, detailed the four priorities for partners as the next steps for Microsoft's fiscal 2021, which started July 1. Microsoft is holding the Inspire conference virtually on Tuesday and Wednesday.
In a keynote called "Partnership Through Pandemic," Schuster heralded the role that partners have played to ensure that their customers could stay in business.
"You're the digital first responders, the unsung heroes, supporting and lifting the frontline workers up as they respond to this crisis. And your speed has been remarkable," Schuster said. "When our world started to change around us, partners did what you do best: Innovate and problem-solve using technology to help customers figure stuff out."
Schuster says that the initial phase of enabling organizations to support remote work environments were coincidentally set up by the work Microsoft and partners had been doing for the previous 18 months -- in terms of ongoing migrations to Office 365 and Microsoft Azure, as well as partners having gotten trained and proficient on Teams and Windows Virtual Desktop.
Judson Althoff, executive vice president of Worldwide Commercial Business at Microsoft, piggybacked on the theme in his keynote by emphasizing how priorities have changed radically -- for customers and for Microsoft -- over the last few months. "If it looked good to get out of your datacenter pre-COVID, it looks great to get out of your datacenter now," Althoff said. "If you think about it, we've seen more digital transformation happen out of necessity over the last two months than we've seen in the last two years alone."
Althoff also endeavored to impart meaning to the efforts of partners amid the overlapping public health, economic and societal crises. The name of his keynote was "Purpose-Driven Digital," and he defined the effort as "the art and science of leveraging technology innovation to drive business and societal outcomes for good."
As another example of the kind of effort that fits the purpose-driven digital theme but has been put on the back burner because of more recent events is Microsoft's ecological initiative. The effort was announced earlier this year with big goals for carbon-neutral and carbon-negative milestones for both Microsoft and its ecosystem, and a few months ago probably could have been expected to be a big theme at Inspire. On Tuesday, Althoff mentioned the environment in passing as something Microsoft and its partners could address under his framework. (Microsoft did provide details on progress with the initiative here.)
Schuster positioned the four priorities -- remote work, business continuity, security and cloud migration -- as a continuation of the critical work partners have been doing in the pandemic, and an opportunity to transition their businesses.
"This pandemic has changed the way we work forever," Schuster said. "From a partner perspective, this moment unlocks a huge opportunity to come in with a change-management and managed-services mindset."
Schuster said that in a follow-up session on Wednesday she would detail investments that Microsoft is making in each of those areas. Also speaking on Wednesday are Microsoft CEO Satya Nadella and Microsoft President Brad Smith.
One partner found Microsoft's FY '21 priorities to be consistent with Microsoft's pre-coronavirus initiatives and to be sensible, as far as they go.
Migration to cloud, for example, is certainly a pre-coronavirus priority that has increased in importance in recent months, said Ric Opal, a principal at BDO Digital who leads strategic partnerships and national go-to-market efforts. "It's true, but it's vague. They want migration to the cloud in the advanced workloads," Opal said in reference to applications tied to platform-as-a-service (PaaS) versus virtual machines that can easily be ported to a competitor's cloud. "Ultimately, they want them to be sticky. I want the same thing. I want sticky customers."
Opal also sees potential in security but contends compliance will be just as important in many cases. "We feel organizationally that a lot of people raced to get remote. Probably in going remote, they didn't care for security and compliance as much as they should have," Opal said. "Our viewpoint would be that compliance is a huge deal."
Posted by Scott Bekker on July 21, 20200 comments
The 2020 Microsoft Partner of the Year Awards are filled with stories of Microsoft partners rapidly retooling their offerings or crafting bespoke solutions to meet the urgent pandemic-related needs of customers -- from companies to nonprofits to government agencies.
Microsoft on Monday released the list of winners of the 2020 Microsoft Partner of the Year awards, which included winners in 49 categories, finalists and country-level winners.
Microsoft channel chief Gavriella Schuster called partners' efforts inspirational in their ability and willingness to meet the moments of the last few months.
"Through it all, our partners have been working and innovating, building technologies across the intelligent cloud and intelligent edge that allow organizations of all types to connect, operate, and carry on. We've seen amazing displays of agility and creativity as partners navigate a new world for their businesses, while still supporting customers and building new products and services," Schuster said in a blog congratulating the winners. The Monday announcement comes a week before Inspire, Microsoft's annual partner conference which, like most industry events this year, is being held virtually.
The awards process this year was stretched out due to the coronavirus, with the deadline for submissions pushed back by three weeks to May 12. Even with all that partners were going through in their businesses and on behalf of their customers, Microsoft received 3,300 submissions for the awards -- up from 2,900 a year ago, noted Melissa Mulholland, director of Partner Enablement and Profitability for One Commercial Partner at Microsoft.
"Despite COVID-19 and the extension of the deadline, to still have an increase in submissions...is humbling," Mulholland said. That partners from 100 different countries set aside time during the crisis to put together submissions speaks to the marketing and business value of winning the award, she said. "It really signals that they've got a capability as well as success that customers really value."
Like partners who are broadly having success in this challenging environment, many of the award winners shared a common attribute. "It's those that were able to respond with clear solutions, whether it's helping the government in being able to track cases to being able to help schools get remote learning off the ground. [It's really about] coming out with creative and timely solutions," Mulholland said.
One such partner was RedBit Development in Burlington, Ontario, which won the first-ever Community Response Award. That award was created at the same time the award deadline was extended in April, a time when health care, education and business infrastructures were all straining under the weight of the burgeoning pandemic.
"This new award offers recognition to partners that are providing innovative solutions or services to help solve challenges for our customers and community during the COVID-19 pandemic," Schuster said of the award.
RedBit, a software consulting, design and engineering company, won for its work helping Canada's largest food rescue charity, Second Harvest, take its food distribution program national and support a grant portal as the COVID-19 emergency was causing a 40 percent increase in demand from food-insecure families.
"In just three weeks, RedBit rescaled and optimized the FoodRescue.ca platform on Azure, added a feature to enable non-food donations such as hand sanitizer and toilet paper, and launched a mobile app integrated with Dynamics 365 to make it easier for donors to donate food. On top of all of this, RedBit created a grant portal in under a week, to support the equitable distribution of federal relief funding to appropriate charities across the country," RedBit explained in a post about its Inspire Award submission.
Another social contribution award, Microsoft Partner of the Year for Social Impact, also went to a partner dealing with a COVID-19-related emergency for a nonprofit organization with a mission to empower young people through recreation and community building.
"With COVID-19, the nonprofit had to close 90 percent of its operations and stand down thousands of critical workers. When the Australian Government launched the 'Job Keeper' program to help COVID-affected organizations continue paying for staff wages, the organization needed to process over 5,000 employee records in a short timeframe to obtain the much-needed funding securely and compliantly," Microsoft's description of Barhead Solutions' winning entry read. "Within two days, Barhead and the nonprofit partnered to build a PowerApp leveraging Microsoft Power Platform to process the employee records, thereby ensuring 5,000+ employees were paid during this global pandemic including cooks and catering assistants, housekeepers and coaches."
Among the many other coronavirus-related solutions in the winning entries were:
- Accenture/Avanade in the United Kingdom won "Modern Workplace for Firstline Workers." Working with national health organizations to help care teams stay connected from a safe social distance, the partner used Teams and Microsoft Bookings in separate solutions. Accenture/Avanade created "Nightingale Connect," a collaboration service enabled by Teams to allow an emergency temporary hospital system to coordinate operations nationally. The Microsoft Bookings solutions allowed doctors and patients to have virtual visits.
- Rapid Circle in the Netherlands won the "Teamwork" award for, among other things, spinning up a Teams application in one weekend that helped a hospital assess the suitability and availability of hospital beds. The application delivered savings in time and costs that Rapid Circle was able to turn into a repeatable solution for other health care businesses.
- PTC in the United States won the "Manufacturing" award for an augmented reality effort that helped ramp up production of ventilators needed for treating severely ill COVID-19 patients. PTC's solution is called Vuforia Expert Capture. From the Microsoft award description: "The UK government approached a consortium of industry partners for assistance with rapid manufacturing of ventilators amidst the COVID-19 pandemic. PTC and Microsoft provided Vuforia Expert Capture on Azure and HoloLens2 to record the entire ventilator build process and create supporting material at no cost. The outcome successfully increased peak output of 50 units per week to 1,500 units per week."
- Leading Learning Partners Association (LLPA) in the Netherlands won the "Learning" category with a rapid retooling of its training procedures. "In a matter of days, 52+ countries quickly mobilized from in-person classroom training to virtual and hybrid deliveries due to COVID," the Microsoft description for LLPA read.
Modern Workplace Award Winners
Apps and Solutions for Microsoft Teams
- Winner: Klaxoon (France)
- Finalist: AkariSolutions Ltd.
- Finalist: AskMeWhy
- Finalist: ThoughtWireCorporation
Calling and Meetings for Microsoft Teams
- Winner: Continuant (United States)
- Finalist: Communicativ| de Teams Specialist
- Finalist: Enabling Technologies Corporation
- Finalist: Orange Business Services Global
Modern Endpoint Management
Modern Workplace for Firstline Workers
- Winner: Accenture/Avanade Inc. (United Kingdom)
- Finalist: Cognizant Technology Solutions US Corporation
- Finalist: Long View Systems Corporation
- Finalist: SnapNetLimited
Project and Portfolio Management 2020
- Winner: ProActiveA/S (Denmark)
- Finalist: PROJECTUM ApS
- Finalist: WicresoftNorth America
- Finalist: Sensei Project Solutions
Security and Compliance
- Winner: Threatscape Limited (Ireland)
- Finalist: Delphi Consulting
- Finalist: Glück & KanjaConsulting AG
- Finalist: ThirdSpaceLtd.
Teamwork
- Winner: Rapid Circle (Netherlands)
- Finalist: AkariSolutions Ltd
- Finalist: RSM Product Sales LLC
Business Applications Award Winners
Dynamics 365 Business Central
- Winner: NAB Solutions AB (Sweden)
- Finalist: ABC GROUP B.V.
- Finalist: Cooper Parry Group Ltd
- Finalist: WiiseSoftware Pty Ltd
Proactive Customer Service
Connected Field Service
- Winner: Accenture/Avanade Inc. (Germany)
- Finalist: Content and Code
- Finalist: Hitachi Solutions America Ltd.
- Finalist: HSO Nederland B.V.
- Finalist:RSM Product Sales LLC
Modernize Finance and Operations
- Winner: HSO (Netherlands)
- Finalist: Accenture/Avanade Inc.
- Finalist: Fullscope Inc.
- Finalist: GWS Gesellschaft für
- Finalist: Warenwirtschafts-Systeme mbH
Intelligent Sales and Marketing
PowerApps and Power Automate
Power BI
- Winner: Slalom Consulting (United States)
- Finalist: Cognizant Technology Solutions US Corporation
- Finalist: Pragmatic Works Software Inc.
- Finalist: Tallan Inc.
Azure Award Winners
AI and Machine Learning
- Winner: Accenture/Avanade Inc. (United States)
- Finalist: Altius
- Finalist: Axilion Ltd.
- Finalist: Concurrency Inc.
Application Innovation
Azure Influencer
- Winner: ReadyMind (Mexico)
- Finalist: FCamaraConsultoria e Formação
- Finalist: Neudesic
- Finalist: Slalom Consulting
Data Analytics
- Winner: Informatica (United States)
- Finalist: Catapult Systems
- Finalist: Infosys Limited
- Finalist: CAPGEMINI Technology Services SAS
Data Estate Modernization
- Winner: Wipro Technologies - Global HQ (Switzerland)
- Finalist: Cognizant Technology Solutions Philippines Inc.
- Finalist: Tata Consultancy Services Ltd.
- Finalist: TimeXtenderUS
Datacenter Migration
- Winner: DXC Technology Services (United States)
- Finalist: Infosys Limited
- Finalist: Intercept
- Finalist: Cognizant Worldwide Limited
DevOps
- Winner: Accenture/Avanade Inc. (United States)
- Finalist: Arinco
- Finalist: Embee Software Pvt. Ltd.
- Finalist: LARSEN & TOUBRO INFOTECH LIMITED
Internet of Things
- Winner: Mariner (United States)
- Finalist: Cognizant Technology Solutions US Corporation
- Finalist: Iconics Inc.
- Finalist: Tata Consultancy Services Ltd.
Mixed Reality
- Winner: Taqtile Inc. (United States)
- Finalist: 北京商询科技有限公司
- Finalist: Meemim Inc.
- Finalist: Trimble Inc.
OSS on Azure
SAP on Azure
Industry Award Winners
Automotive
- Winner: JDA Software - Global (United States)
- Finalist: ERICSSON ARASTIRMA GELISTIRME
- Finalist: VE BILISIM H A.S.
- Finalist: Linker Networks
- Finalist: Technosoft(SEA) Pte. Ltd.
Education
- Winner: DuggaAB (Sweden)
- Finalist: Applied Cloud Systems (ACS) (joint nominee)
- Finalist: Business IT
- Finalist: HaldorAB
- Finalist: NetApp
Energy
- Winner: Ernst & Young LLP (United States)
- Finalist: Envision Group
- Finalist: Esri
- Finalist: Seeq Corporation
Financial Services
- Winner: Ernst & Young LLP (United Kingdom)
- Finalist: UIPathNew York
- Finalist: PowerObjects-An HCL Technologies Company
- Finalist: Finastra
Government
- Winner: Cognizant Worldwide Limited (United Kingdom)
- Finalist: Accenture Spain/Avanade Spain (joint nominee)
- Finalist: Genetec Inc.
- Finalist: Knowledgelake Inc.
Health Care
- Winner: Accenture/Avanade Inc. (United States)
- Finalist: apoQlarGmbH
- Finalist: Illuminance Solutions
- Finalist: WWT
Manufacturing
- Winner: PTC (United States)
- Finalist: Blue Yonder (formerly JDA Software)
- Finalist: Icertis Inc.
- Finalist: AVEVA Solutions Limited
Media and Communications
- Winner: CSG Systems Inc. (United States)
- Finalist: AdPushup Inc.
- Finalist: Avid Technology Inc.
- Finalist: Teradici Corporation
Retail
Other
Advisory Services
Alliance Global SI
Alliance Global ISV
- Winner: Adobe Systems Inc. (United States)
- Finalist: VMware Inc.
- Finalist: Icertis Inc.
- Finalist: HashiCorp
Customer Experience
- Winner: Insight North America (United States)
- Finalist: CodeTwo Sp. z o.o. Sp.k.
- Finalist: Quadrasystems.net (India) P Ltd.
Community Response
- Winner: RedBitDevelopment (Canada)
- Finalist: ACS
- Finalist: FiveP Australia Pty. Ltd.
- Finalist: NetApp
- Finalist: NTT DATA Philippines Inc.
Diversity and Inclusion Changemaker
- Winner: AkariSolutions Ltd. (United Kingdom)
- Finalist: BIG BRAIN CONSULTING LTDA
- Finalist: RedManeTechnology LLC
- Finalist: Concurrency Inc.
Indirect Provider
- Winner: Ingram Micro (United States)
- Finalist: Crayon AS
- Finalist: Rhipe Limited
- Finalist: Tech Data Corporation
Learning
Partner for Social Impact
Global SI Digital Transformation
- Winner: KPMG (Global)
- Finalist: Cognizant
- Finalist: Infosys
Commercial Marketplace
- Winner: Fortinet (United States)
- Finalist: Flashgrid Inc.
- Finalist: Barracuda Networks
- Finalist: Check Point HQ United States
Microsoft for Startups
- Winner: Uncrowd (United Kingdom)
- Finalist: Egress
- Finalist: ThroughPut Inc.
- Finalist: Web3 Labs
Solution Assessment
- Winner: Unify Cloud LLC (United States)
- Finalist: 10th Magnitude
- Finalist: INSIGHT ENTERPRISES AUSTRALIA PTY LTD
Surface Hub
Surface PC
- Winner: CDW Logistics Inc. (United States)
- Finalist: 株式会社大塚商会
- Finalist: Bechtle Logistik & Service GmbH
- Finalist: Softcat Plc.
Posted by Scott Bekker on July 14, 20200 comments
A new survey-based security research report suggests that seven in 10 organizations have experienced public cloud security incidents in the last year.
U.K.-based security company Sophos released its report, "The State of Cloud Security 2020," this week. The findings are significant due to the substantial sample size of the survey, with responses from more than 3,500 IT managers in 26 countries.
Conducted in January and February, the survey doesn't allow for any conclusions about changes in attack patterns since the coronavirus pandemic forced a shift to remote work, with its increased reliance on public cloud platforms. However, the survey reveals eye-opening trends about how common public cloud security incidents were already becoming at the beginning of this calendar year.
"Seventy percent of respondents said they had suffered a public cloud security breach in the last year," the report states. "This is extremely worrisome for organizations, with 96% of the 3,521 respondents expressing concern about their current level of security across the six major public cloud platforms."
For purposes of the survey, Sophos focused its definition of public cloud on Microsoft Azure, Oracle Cloud, Amazon Web Services (AWS), VMware Cloud on AWS and Alibaba Cloud. In addition, some respondents were also using Google Cloud and IBM Cloud.
As for how attackers are getting in, a third of the survey respondents attributed incidents to having cloud account credentials stolen. The other two-thirds of breaches resulted from a security misconfiguration. Of the misconfigurations, 22 percent involved cloud resource misconfigurations and 44 percent occurred at the Web application firewall.
Organizations using multiple public clouds may be having more trouble than those concentrating on a single cloud, the survey suggests. " Security risks inevitably multiply as organizations expand their number of cloud environments. Seventy-three percent of the organizations surveyed were using two or more public cloud providers and reported up to twice as many security incidents as those using one cloud platform," according to the report.
The full report is available here.
Posted by Scott Bekker on July 09, 20200 comments
With the help of federal courts, Microsoft is seizing domains to try to slow a "sophisticated, new phishing scheme" that is employing pandemic-related messaging against customers in 62 countries.
Microsoft published a blog about the effort on Tuesday, the same day that the U.S. District Court for the Eastern District of Virginia unsealed documents from Microsoft's lawsuit.
"Our civil case has resulted in a court order allowing Microsoft to seize control of key domains in the criminals' infrastructure so that it can no longer be used to execute cyberattacks," said Tom Burt, Microsoft corporate vice president for customer security and trust, in the blog post.
The Microsoft Digital Crimes Unit first got wind of the malicious activity, which it classifies as a business e-mail compromise attack, in December, although at that time the attack's messaging did not incorporate COVID-19 themes.
Back then, Microsoft had employed technical measures to block the attacks. Without saying so explicitly, Burt's blog implies that criminals ramped up their effort as they realized that worldwide concerns over COVID-19 could lower individual executives' routine wariness of suspicious messages and attachments.
"In cases where criminals suddenly and massively scale their activity and move quickly to adapt their techniques to evade Microsoft's built-in defensive mechanisms, additional measures such as the legal action filed in this case are necessary," Burt wrote.
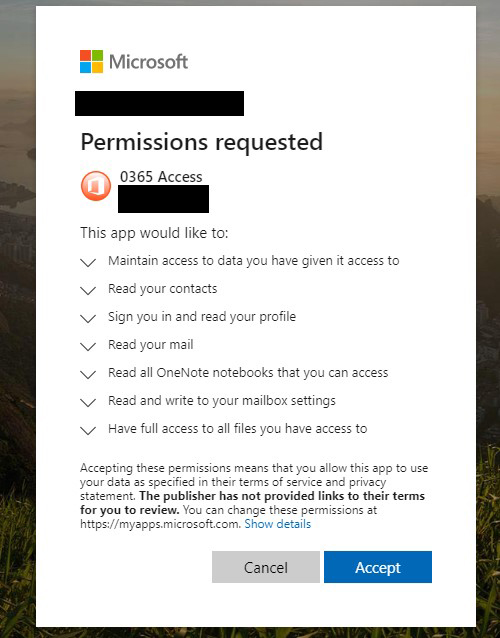 Users clicking on an attachment or a link in what Microsoft is calling a sophisticated new phishing attack would be prompted to grant the attacker a number of dangerous permissions. (Source: Microsoft)
Users clicking on an attachment or a link in what Microsoft is calling a sophisticated new phishing attack would be prompted to grant the attacker a number of dangerous permissions. (Source: Microsoft)
Like most phishing attacks, there were several parts to this attack. The cybercriminals designed phishing e-mails to look like they originated internally. Subject lines and message body text involved pandemic-related financial concerns. A key element of this attack was malicious links, such as an apparent Office attachment with a filename like "COVID-19 Bonus."
Clicking on the deceptive link led to a prompt from a malicious Web application asking the user to grant various permissions. As shown in a consent screen included in the Microsoft blog, the user could be allowing the attacker to access data, read contacts, read mail, view OneNote notebooks, send mail and get full file access.
The attack differs from simpler phishing attacks, which might send users to a sign-in screen, where they would be prompted to enter a user name and password to access the file or follow the link, and where small mistakes or inconsistencies in the interface might give users clues not to click any further.
Burt said the civil case allowed Microsoft to "proactively disable key domains that are part of the criminals' malicious infrastructure."
Microsoft also recommended that organizations protect themselves by enabling two-factor authentication on e-mail accounts, reviewing how to spot phishing schemes, enabling security alerts about links and files from suspicious Web sites and checking e-mail forwarding rules for suspicious activity.
Posted by Scott Bekker on July 07, 20200 comments
Researchers at Menlo Security on Tuesday documented newly discovered attacks in the wild leveraging an old flaw in Microsoft Office -- underscoring once again the importance of applying older patches.
Microsoft first patched the vulnerability, CVE-2017-11182, in late 2017. The flaw is in the Equation Editor of Microsoft Office, which allows users to embed mathematical equations or formulas inside Office documents.
A small number of attacks turned up in Menlo Security's regular operations over a two-week period in late May and early June. The company offers cloud proxy with isolation, executing browsing and documents in its remote browsing solution to prevent active content from hitting a customers' endpoints.
Menlo detected three different attacks against five companies, all using the Equation Editor flaw but each attempting to deliver a different Remote Access Trojan. None of the attacks, which were found in Hong Kong and in North America and involved real estate, entertainment and banking targets, went out to more than two employees at a single company.
"We think that it was targeted and it was targeting very few important individuals," said Vinay Pidathala, director of security research at Menlo Security, in an interview. "We believe they did the reconnaissance and they targeted the individuals."
The finding reinforces and amplifies the advice from the CISA and the FBI last month listing the 10 vulnerabilities most routinely exploited by "foreign cyber actors." CVE-2017-11882 was high on that list. In fact, the FBI singled out the Equation Editor flaw as a favorite of state-sponsored attackers.
"Of the top 10, the three vulnerabilities used most frequently across state-sponsored cyber actors from China, Iran, North Korea, and Russia are CVE-2017-11882, CVE-2017-0199, and CVE-2012-0158. All three of these vulnerabilities are related to Microsoft's OLE technology," the CISA/FBI alert noted.
The agencies then called on the private sector to patch the threats to help with U.S. network security. "A concerted campaign to patch these vulnerabilities would introduce friction into foreign adversaries' operational tradecraft and force them to develop or acquire exploits that are more costly and less widely effective."
On a separate trend, Pidathala noted that the three specific attacks all hosted their payloads on SaaS platforms, including Microsoft OneDrive.
"As enterprises are moving to the cloud, they're adopting cloud storage solutions like Box, Dropbox and OneDrive. By posting their malware on these websites, [attackers] are able to make it more believable. Also, a lot of security appliances might whitelist or might not inspect traffic that comes from OneDrive, because it's a trusted source. So by hosting their weaponized payloads on these popular platforms, they're able to get by," Pidathala said.
For more detail on the attack and the RATs involved, visit Pidathala's blog post here.
Posted by Scott Bekker on June 30, 20200 comments
As part of a broad racial justice initiative involving several hundred million dollars, Microsoft is committing $73 million to support Black and African American-owned partners in the United States.
Microsoft CEO Satya Nadella shared details of the initiative this week in a blog entry called "Addressing Racial Injustice," and said senior Microsoft executives and board members have been evaluating options over the last few weeks. The blog is Nadella's second on racial justice since the death of George Floyd in Minneapolis sparked mass protests against police violence.
"Today, we are making commitments to address racial injustice and inequity for the Black and African American community in the United States. We will additionally take important steps to address the needs of other communities, including the Hispanic and Latinx community, across the company in the next five years," Nadella wrote Tuesday.
For partners, Nadella committed to boosting the number of Black and African American-owned partner companies in the United States.
"We know how important partners are to the growth of our business. We look forward to investing to increase the number of Black- and African American-owned partners in our US partner community by 20 percent over the next three years," Nadella said.
Three pools of money are being set aside to accomplish that goal, Nadella said.
For startup partners, a new $50 million partner fund will be created to help provide access to capital. The loans will be provided through the startup phase and "be recovered over time as their business grows."
Existing and new partners will have access to $20 million in financing to support cash flow needs. Recent research across the economy has shown the fund to be addressing a need. A working paper from the Stanford Institute for Economic Policy Research found that African-American small businesses were the hardest-hit by coronavirus-related social distancing restrictions and demand shifts. While the study found a 22 percent drop in business owners from February to April 2020, the damage was much worse within the African-American community.
"African-American businesses were hit especially hard experiencing a 41 percent drop. Latinx business owners fell by 32 percent, and Asian business owners dropped by 26 percent," report author Robert Fairlie wrote.
Although Nadella's post did not lay out details for the Latinx community, the same Stanford report noted that Latinx business owners fell by 32 percent.
Microsoft also committed to an additional $3 million "in training programs covering financial management, tech solutions, and go-to-market readiness," Nadella said.
The partner funding is a small part of Microsoft's overall program.
A very large bucket of money is going into an initiative that will help Microsoft partners who are also Microsoft suppliers. Microsoft plans to double the number of Black- and African American-owned approved suppliers over the next three years. The effort will be supported with an incremental $500 million in spending with those existing and new suppliers, Nadella said. "We will also encourage Black and African American representation progress in our top 100 suppliers, which account for over 50 percent of our indirect spend, by requesting annual disclosure of their diversity profile information (e.g., workforce diversity, goals) that we will incorporate into our RFP evaluations," he said.
The company is adding $150 million to its diversity and inclusion spending with a goal of doubling the number of Black and African American people managers, senior individual contributors and senior leaders in the United States by 2025. Microsoft and other tech giants have been getting criticism lately for slow progress on diversification despite high-profile PR announcements in recent years.
As part of an effort to support Black- and African American-owned financial institutions, Microsoft is also creating a $100 million program to invest with Minority Owned Depository Institutions (MDIs). The company also is creating a $50 million investment fund focused on supporting Black- and African American-owned small businesses across the economy, in addition to the partner-focused funding.
Posted by Scott Bekker on June 24, 20200 comments
A major new survey of managed service providers (MSPs) finds that revenues are down, customers are struggling to pay their bills and interest in mergers and acquisitions is flagging in the midst of COVID-19's twin health and economic crises.
IT Glue, an IT documentation provider for IT professionals and MSPs, released results of the survey on Monday. Originally fielded in February with 1,500 participants, IT Glue conducted a follow-up survey in May to gauge sentiment after the effects of the pandemic had begun to hit the United States, which is home to about three-quarters of the respondents. That follow-up survey had about 500 respondents.
"The pandemic has created an unprecedented landscape for all businesses," said Nadir Merchant, general manager of IT Glue, which was acquired by MSP powerhouse Kaseya in December 2018.
At a high level, the report described the effect of COVID-19 on MSPs' business this way: "We know that the work from home scramble in March was replaced by a slowdown in April. In our follow-up survey, we found that around half of MSPs saw their monthly revenue decrease as the result of the coronavirus shut down, though some MSPs reported an increase in revenue as well."
In other words, MSPs that felt the slowdown in business definitely weren't alone. The specific number reporting monthly revenue decreases was 51 percent.
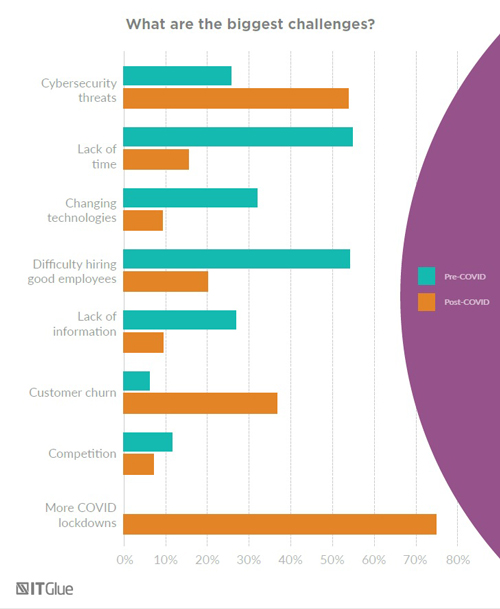 A chart from IT Glue's survey report shows how drastically MSPs' priorities have changed between February and March of this year. (Source: "2020 Global MSP Benchmark Report: A Pre and Post COVID Analysis," IT Glue)
A chart from IT Glue's survey report shows how drastically MSPs' priorities have changed between February and March of this year. (Source: "2020 Global MSP Benchmark Report: A Pre and Post COVID Analysis," IT Glue)
A slowdown in pay, or customers being outright unable to pay, also showed up in the follow-up survey. Some 29 percent of MSPs reported seeing their accounts receivable increase. A few MSPs reported that their accounts receivable impact increased by 50 percent or more. Just under 40 percent said their accounts receivable was flat. A surprising 23 percent had their accounts receivable impact decline, the survey found.
As MSPs deal with pandemic-related issues, interest in mergers and acquisitions has taken a big hit. Having done this survey for three years, IT Glue noted a major shift in the number of firms that expressed "no interest" in M&A. "While this figure has been steadily rising, the pandemic has marked the most profound shift in M&A sentiment in the MSP space," the report stated.
In the February run of the survey, 48 percent of respondents were not considering acquiring or merging with another MSP. By May, that figured had soared to 63 percent.
That's the buy side. On the sell side, sentiment is even more heavily anti-M&A. In February, 73 percent were not looking to sell. By May, that figure was 85 percent.
There were also major change in the challenges that MSPs considered important from February to May.
Cybersecurity threats, already a major concern for MSPs, approximately doubled from 27 percent to more than 50 percent. Customer churn also went way up as a concern. Going the other way were concerns about challenges related to lack of time, difficulty hiring good employees and changing technologies.
Meanwhile, 74 percent of respondent MSPs in May saw the potential for a renewed lockdown in the fall as a major challenge.
Posted by Scott Bekker on June 15, 20200 comments
Microsoft President Brad Smith said Thursday that the artificial intelligence platform powerhouse won't be selling facial recognition technology to U.S. police departments until there is a national law in place that is "grounded in human rights."
Smith's statement comes after IBM and Amazon both took similar positions in the wake of worldwide protests against police brutality and racism in policing sparked by the death of George Floyd. Those moves by Microsoft's AI peers led critics to call on Microsoft this week to take public steps, as well.
Speaking in a live interview with Washington Post columnist David Ignatius on Thursday, Smith emphasized that Microsoft already was not selling facial recognition technology to police, but suggested the company would also use its influence to push for Congressional legislation.
"We've decided that we will not sell face recognition technology to police departments in the United States until we have a national law in place grounded in human rights that will govern this technology," Smith said. "If all of the responsible companies in the country cede this market to those that are not prepared to take a stand, we won't necessarily serve the national interest or the lives of the black and African American people of this nation well."
In a letter to Congress Monday, IBM CEO Arvind Krishna said IBM was getting out of the business of general purpose facial recognition or analysis software.
"IBM no longer offers general purpose IBM facial recognition or analysis software. IBM firmly opposes and will not condone uses of any technology, including facial recognition technology offered by other vendors, for mass surveillance, racial profiling, violations of basic human rights and freedoms, or any purpose which is not consistent with our values and Principles of Trust and Transparency. We believe now is the time to begin a national dialogue on whether and how facial recognition technology should be employed by domestic law enforcement agencies," Krishna wrote.
In a statement on Wednesday, Amazon declared a one-year moratorium on police use of its Rekognition platform for facial recognition. "We've advocated that governments should put in place stronger regulations to govern the ethical use of facial recognition technology, and in recent days, Congress appears ready to take on this challenge. We hope this one-year moratorium might give Congress enough time to implement appropriate rules, and we stand ready to help if requested," the Amazon statement read.
A day after calling on Microsoft to speak out, Electronic Frontier Foundation (EFF) Policy Analyst Matthew Guariglia, updated his post to call Microsoft's Thursday announcement a good step. "But," he continued, Microsoft must permanently end its sale of this dangerous technology to police departments."
Here's a longer transcript of Smith's comments to the Washington Post:
We have been focused on this issue for two years and we have been taking a principled stand and advocating not only for ourselves but for the tech sector and under the law a principled stand for the country and for the world.
As a result of the principles that we put in place, we do not sell facial recognition technology to police departments in the United States today.
But I do think this is a moment in time that really calls on us to listen more, to learn more, and most importantly, to do more. Given that, we've decided that we will not sell face recognition technology to police departments in the United States until we have a national law in place grounded in human rights that will govern this technology.
We'll also put in place some additional review factors so that we're looking at other potential uses of this technology that go even beyond what we already have for other potential scenarios.
The number one point that I would really underscore is this. We need to use this moment to pursue a strong national law to govern facial recognition that is grounded in the protection of human rights.
I think it is important to see what IBM has done. I think it is important to recognize what Amazon has done. It is obviously similar to what we are doing. But if all of the responsible companies in the country cede this market to those that are not prepared to take a stand, we won't necessarily serve the national interest or the lives of the black and African American people of this nation well.
We need Congress to act, not just tech companies alone. That is the only way that we will guarantee that we will protect the lives of people."
Posted by Scott Bekker on June 11, 20200 comments
Vectra AI, a surging security company applying artificial intelligence to network-based intrusion detection, on Tuesday unveiled strategic integrations with Microsoft's core security technologies.
The eight-year-old, San Jose, Calif.-based Vectra attracted $100 million in a Series E funding round last June in part due to growing interest in its approach to network threat detection and response (NDR).
Vectra's Cognito platform uses artificial intelligence to help identify attacks coming over the network and over the cloud and deploys easy-to-understand scoring and charting to help professionals in a security operations center (SOC) prioritize the most critical threats and respond to them quickly or automatically based on user-defined rules.
The company is going to market through partnerships with major security players, emphasizing a Gartner-published concept known as the "SOC visibility triad." In Vectra's implementation, the triad consists of the company's own NDR tool for network and cloud visibility, combined and integrated with other vendors' endpoint detection and response (EDR) tools and with partners' security information and event management (SIEM) tools.
In theory, the triad would cast a wider, more comprehensive net for potential attacks while dramatically reducing the signal-to-noise problem with security alerts. Current Vectra partners for other legs of the triad include CrowdStrike, Carbon Black, Cybereason, SentinelOne, ArcSight, IBM, Chronicle and Splunk.
The news on Tuesday is not Vectra's first foray into Microsoft technologies. In February, Vectra launched Cognito Detect for Office 365, which used detection models focused on credentials and privilege in SaaS applications to stop attacks.
But the Tuesday announcement involves working with Microsoft to bring the SOC visibility triad effort to the Microsoft stack. In triad terms, Vectra is the NDR piece, and as of Tuesday, it is integrated with Microsoft Defender Advanced Threat Protection (ATP) for the EDR piece and with Azure Sentinel for the SIEM piece.
The Defender ATP integrations with Vectra combine the cloud/datacenter detections with Microsoft's process-level context from the endpoint, and allow for the isolation or disabling of compromised systems. On the Sentinel side, Vectra created custom workbooks in Azure Sentinel that bring elements of their dashboard into Microsoft's cloud SIEM product.
By working with those two strategic components of the Microsoft security mix, Vectra also on Tuesday joined the Microsoft Intelligent Security Association (MISA), a group of more than 80 members with deep programmatic hooks into a dozen Microsoft security technologies or products. In addition to Defender ATP and Azure Sentinel, the MISA-related technologies include Azure Active Directory, Azure Information Protection, Microsoft Endpoint Manager, Microsoft Graph Security API, Microsoft Cloud App Security, Azure Security Center, Azure Security Center for IoT Security, DMARC reporting for Microsoft 365, Windows antimalware platform and Azure DDOS Protection.
Posted by Scott Bekker on June 09, 20200 comments