Security researchers have discovered a logical flaw in the Credential Security Support Provider (CredSSP) protocol that affects all supported versions of Windows.
Preempt Security reported the flaw to Microsoft last August. Microsoft released a fix for it this week as part of its monthly Patch Tuesday release.
The flaw, CVE-2018-0886, was rated "important" by Microsoft, which is a middling severity designation in Microsoft's scale, largely because the new flaw is not an initial infection vector.
Instead, an attacker needs to already be inside the network and set up a man-in-the-middle (MITM) attack via methods that could include ARP Poisoning or even the new WPA2 vulnerability known as KRACK.
CredSSP is designed to securely forward a user's full credentials to a target server. The flaw relies in part on the fact that the client trusts the public key provided by the server. In the case of an RDP connection, an attacker would intercept the initial connection request from the client and return a malicious command to the client, which assumes the command is actually a valid public key from the server and signs it. That signed version is passed by the MITM back to the server, which executes the malicious code -- now signed by the client -- on the server.
Preempt positions the flaw as a technique for lateral movement and privilege escalation. One of the most severe scenarios would be if the attacker intercepts an attempt by an administrator to remotely log on to a domain controller.
"This vulnerability is a big deal, and while no attacks have been detected in the wild, there are a few real-world situations where attacks can occur," said Roman Blachman, Preempt CTO and co-founder, in a statement. Preempt also posted a video showing how the attack works and a technical blog post. "Ensuring that your workstations are patched is the logical, first step to preventing this threat. It's important for organizations to use real-time threat response solutions to mitigate these types of threats," Blachman said.
Dustin Childs of the Zero Day Initiative at Trend Micro described CredSSP as "fascinating" in his analysis of Microsoft's Patch Tuesday release, which included 14 updates resolving 78 unique vulnerabilities. "This patch corrects a truly fascinating bug," Childs wrote of the CredSSP flaw. "It's important to understand this is not a constrained delegation. CredSSP passes the user's full credentials to the server without any constraint. That's a key to how an attacker would exploit the bug."
Childs also warned that applying the patch isn't enough to be fully protected. "Sysadmins must also enable Group Policy settings on their systems and update their Remote Desktop clients. While these settings are disabled by default, Microsoft does provide instructions to enable them. Of course, another alternative is to completely disable RDP, but since many enterprises rely on this service, that may not be a practical solution," he wrote.
Microsoft also released a support document that describes the steps required to update Group Policy or Registry settings to protect against the flaw. In a related step, Microsoft plans to update the Remote Desktop Client next month to provide more detail in error messages when an updated client fails to connect to a server that has not been updated.
A team from Preempt will give a presentation on the vulnerability at Black Hat 2018 Asia next week.
Posted by Scott Bekker on March 14, 20180 comments
Microsoft marked the one-year anniversary of its Teams enterprise chat hub by unveiling new features coming to the service this year, including Cortana integration and a new capability called "Direct Routing."
Originally positioned as Microsoft's answer to Slack, Teams first launched last March as a component of Office 365, which quickly exposed the new platform to the cloud productivity suite's broad base of 120 million users. Microsoft did not provide an update on Monday for how many users Teams has, but the company did report that 200,000 organizations are now using Teams. More recently, Microsoft disclosed that Teams will merge over time with Skype for Business.
After a rough start to 2018 within Microsoft and across the industry, Microsoft's digital voice assistant Cortana will get some attention from Teams engineers at Microsoft. Microsoft plans to add voice integrations within Teams that will allow users to speak with natural language to make a call, join a meeting or add other people to a meeting. The functionality is planned at first for IP phones and conference room devices.
In addition to Cortana integration, other features coming this year include background blur on video, inline message translation, proximity detection for Teams Meetings and mobile sharing in meetings.
The background blur will be an appealing feature for anyone calling into a meeting when they've got an unprofessional scene behind them or a background that they'd otherwise like to keep meeting participants from seeing. Blurring is one approach to the issue. Another approach, from Zoom Video Communications, is a Virtual Background for videoconferencing that allows users to select and display an image, such as a cityscape, behind them during a meeting.
Inline message translation presumably will leverage translation and transcription services in Azure to make posts readable to participants who speak different languages in chats and in channels, which is the Teams term for topic-based discussions among members of a team. With users in 181 Microsoft-defined markets around the world, the translation feature could get heavy use.
The proximity detection feature is designed to help users find and add a Skype Room System. A more universally useful feature will be mobile sharing, which will let attendees share live video streams, photos or their mobile screen.
Microsoft also disclosed a new enterprise calling feature to be available by the end of June called Direct Routing. While the specifics are complicated and have a lot of dependencies on both Microsoft products and third-party infrastructure, Direct Routing will be a way for customers to use existing telephony infrastructure with Teams for calling. In that sense, Direct Routing joins Microsoft Calling Plans as ways for customers to enable calling from Teams. More detail on Direct Routing is available here.
On the anniversary, Microsoft also highlighted some previously disclosed elements of the Teams roadmap. One is cloud recording, a one-click meeting recording option that will automatically transcribe and timecode a meeting. Features include the ability to read captions, search the conversation and play back the meeting. Later, Microsoft plans to add facial recognition to automate attribution of comments to specific attendees. Parts of the calling roadmap that Microsoft highlighted again on Monday included consultative transfer and call delegation.
Although they weren't reinforced on Monday, Microsoft has previously discussed a number of features coming by the end of June. For meetings, those features include broadcast meetings, federated meetings, large meeting support for about 250 participants, a lobby for PSTN callers, Outlook meeting schedules from other platforms, PowerPoint loading and sharing, whiteboard and meeting notes, user-level meeting policies for IT professionals, and e-discovery enhancements.
On the calling side, Microsoft has publicly talked about 2018 availability for call support between Teams and Skype Consumer, distinctive rings, call queues, "do not disturb" breakthrough, forwarding to group, call parking and group call pickup. (For more background on Teams-Skype integration, listen to the Redmond Tech Advisor webcast with Office 365 and SharePoint MVP Christian Buckley from December.)
Posted by Scott Bekker on March 12, 20180 comments
Kali Linux hit the Microsoft App Store this week. It's very nearly been reduced to a one-click install for Windows 10 users, and has clear appeal for experienced users.
But if you're thinking of trying out the infamous and powerful penetration testing Linux distribution for the first time now that it's a free and easy install on Windows, there may be a better way.
Tara Raj, a program manager at Microsoft who works with the Windows Subsystem for Linux (WSL), announced availability of Kali Linux in the Microsoft Store in a blog post on Monday. "We are happy to officially introduce Kali Linux on WSL," Raj wrote. She noted "great interest" in Kali among the WSL community after Offensive Security, the security and training company that maintains Kali Linux, posted a tutorial in January for getting the OS running in WSL.
The app-ified experience within the Microsoft Store simplifies and speeds up the installation process, but, somewhat paradoxically, Kali within the WSL is a far less intuitive experience for a Windows user than running the pentesting distribution on a dedicated system, on a Live USB stick, or in a virtual machine.
 [Click on image for larger view.] Kali Linux pinned to the Windows 10 Start menu.
[Click on image for larger view.] Kali Linux pinned to the Windows 10 Start menu.
Downloading Kali
Downloading Kali from the Microsoft Store is relatively quick. Users who haven't tried the Linux subsystem need to enable WSL first. It's a relatively quick process involving running PowerShell as an admin, pasting in one line of code and restarting the system. (Click here to watch Offensive Security's video setup walkthrough, which includes enabling WSL.)
Next, navigate to the Microsoft Store, search for Kali Linux and press the "Get" button. A short 134MB download later brings a prompt to "Launch" Kali or to "Pin to Start".
Once Kali is launched for the first time, the Microsoft Store process takes care of several steps on the user's behalf. Compared to Offensive Security's January tutorial video for running Kali on WSL, downloading Kali Linux from the Microsoft Store seems like it cuts out about half of the previously required commands.
In as little as a few seconds, a command window opens, the installation finishes, and the user gets a prompt to create a regular user account and enter a password.
 If you load Kali Linux on the Windows Subsystem for Linux, you need to have a pretty good idea of what you intend to do with it.
If you load Kali Linux on the Windows Subsystem for Linux, you need to have a pretty good idea of what you intend to do with it.
Now What?
This is the spot where Kali Linux on WSL is less intuitive for a Windows native than actually running Kali in a full-on Linux environment would be, for several reasons.
First, once Kali Linux is installed on Windows, you're looking at a blinking command-line cursor. This is an unforgiving command-line environment where you need to have a rock-solid understanding of Linux commands and Linux file structures in order to do anything.
By comparison, Kali in its native Linux environment actually boots into an attractive GUI. Power users may want to operate primarily in the terminal, but beginners can point and click, navigate files and folders graphically, and explore the interface.
The next way the WSL version is limiting for new users is spelled out in the Microsoft Store description: "This image contains a bare-bones Kali Linux installation with no penetration testing tools -- you will need to install them yourself." Users must know what penetration testing tools to look for, where to find them, and how to download and install them.
The default Kali Linux installation, on the other hand, is an inviting interface that encourages exploration. Dozens of attack tools are preloaded and organized logically by function. A user can drag down the Applications menu in the upper-left and browse tools for Information Gathering, Vulnerability Analysis, Password Attacks, Wireless Attacks, Exploitation Tools, Social Engineering Tools and others.
 [Click on image for larger view.] The full version of Kali Linux on a dedicated machine is, ironically, a much friendlier environment for a Windows user than the Windows Subsystem for Linux version.
[Click on image for larger view.] The full version of Kali Linux on a dedicated machine is, ironically, a much friendlier environment for a Windows user than the Windows Subsystem for Linux version.
One other caveat in the WSL version mentioned in the Microsoft Store description: "Some tools may trigger antivirus warnings when installed, please plan ahead accordingly." For example, the endpoint protection software on my system was not a fan of several files that Kali WSL tried to download while installing Metasploit, such as Trojan.Gen.2, OSX.Trojan.Gen, Meterpreter or Hacktool, among others. They all got quarantined and, I suspect, prevented Metasploit from launching properly.
For users with intermediate-level Linux skills and strong familiarity with the capabilities of various penetration testing tools in Kali Linux and how to load those tools, this app is a great addition to the Windows Store. It has simplified installation and has brought Kali Linux squarely into the everyday Windows desktop. If you know what you're doing and what you want to do, it can be handy to have that Kali terminal running right inside your Windows environment for easy access.
For those who haven't used Kali much or at all and are interested in learning what its frightening and impressive capabilities might reveal about the security of their corporate environments, the WSL version is less useful. In that case, it's still worth the trouble of jumping through the installation hoops to get a regular Kali environment running on a dedicated physical machine or virtual machine.
Posted by Scott Bekker on March 07, 20180 comments
The PC and smartphone markets stumbled in 2017 even while servers went on a tear, according to recent data from market researcher IDC.
With most of the publicly traded vendor companies having already released their quarterly financial reports (with all those reports' attendant clues), IDC released a slew of research this week recapping the fourth quarter.
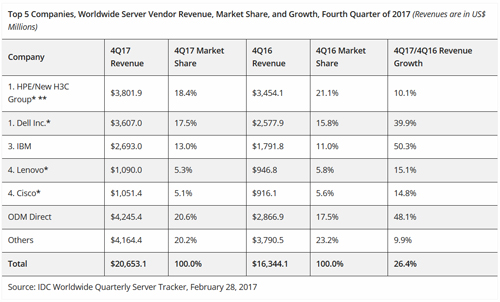
Server market revenues jumped 26 percent year over year to $20.7 billion in the fourth quarter. IDC attributed the momentum to several factors, such as traction for the Purley-based offerings from Intel and the EPYC-based offerings from AMD. The overall server market showed some signs of life, as well, with server shipments increasing nearly 11 percent to 2.84 million units for the quarter.
Yet the factor propping up the server market overall remains the shift in computing from distributed at client sites to centralized at megavendor datacenters.
"Hyperscalers remained a central driver of volume demand in the fourth quarter with leaders such as Amazon, Facebook, and Google continuing their datacenter expansions and updates," said Sanjay Medvitz, senior research analyst for servers and storage at IDC, in a statement. "ODMs [original design manufacturers] continue to be the primary beneficiaries from hyperscale server demand. Some OEMs are also finding growth in this area, but the competitive dynamic of this market has also driven many OEMs such as HPE to focus on the enterprise."
By manufacturer, the HPE/New H3C Group joint venture was tied with Dell for the quarterly revenue lead, followed by IBM, Lenovo and Cisco. Taken as a group, ODM Direct vendors had a slightly bigger share of revenues than either of the leaders.
 [Click on image for larger view.]
[Click on image for larger view.]
The picture for personal computing devices, which IDC defines as desktops, notebooks, slates and detachables, wasn't as positive. IDC is projecting that for the full year of 2017, shipments within the sector declined 2.7 percent. IDC published forecasts out through 2022, and expects compound annual growth for the entire sector to be a paltry 0.1 percent over the period. Short-term, IDC is looking for another drop in 2018 of a little more than 3 percent, with slight pickups thereafter due to corporate refresh cycles, and the ongoing popularity of detachables like the Microsoft Surface.
As for smartphones, IDC reports that 2017 marks the first year-over-year decline for the devices, which are now in a two-horse race between Android and iOS. The 1.46 billion devices that IDC estimates shipped in 2017 represented a half-a-percent drop in volume compared to 2016. Through 2022, IDC forecasts a compound annual growth rate of a little under 3 percent.
Posted by Scott Bekker on March 02, 20180 comments
The years-long tangle between Microsoft and U.S. regulators regarding the extent to which the tech giant can legally protect its customers' privacy against government data requests came to a head on Tuesday.
In a lively one-hour discussion, U.S. Supreme Court justices sparred with lawyers from Microsoft and the U.S. government, covering topics from ranging from privacy rights to latency issues to robots conducting overseas seizures.
At the center of the debate was the question of whether a U.S. court can order a U.S.-based e-mail service provider to comply with a probable-cause-based warrant issued under the 1986 Stored Communications Act (SCA) by disclosing e-mails that the provider has stored abroad.
State of play leading up to the Supreme Court has Microsoft ahead and playing defense. The case started with a Drug Enforcement Agency investigation in 2013. Federal agents persuaded a magistrate judge in the Southern District of New York to issue a warrant for a suspect's e-mails. Microsoft fought the order on the grounds that the e-mails were stored at its datacenter in Ireland. A U.S. District Court rejected Microsoft's appeal, but the U.S. Court of Appeals for the 2nd District ruled in Microsoft's favor.
Discussion on Tuesday settled over and over on a few key topics: the many ways that the outdated SCA is woefully inadequate for the cloud era; whether the court should simply wait for pending congressional legislation to make the questions in the case moot; justices seeking clarification on what exactly happens in the United States and abroad when Microsoft or other service providers produce an e-mail record; domestic versus extraterritorial jurisdiction questions; and back-and-forth about the legal differences between warrants, subpoenas, orders, searches and disclosures.
What Microsoft wants is for the Supreme Court to leave the issue alone and to hope that Congress passes the CLOUD Act, introduced recently with bipartisan and tech industry support.
"There were conversations about where the Internet is headed," Microsoft lawyer E. Joshua Rosenkranz said Tuesday in his closing statement. "There [are] conversations about whether this will kill the tech sector, how much of an international consensus there is about the sovereignty of data. These are all questions that only Congress can answer. Meanwhile, this Court's job is to defer, to defer to Congress to take the path that is least likely to create international tensions. And if you try to tinker with this, without the tools that -- that only Congress has, you are as likely to break the cloud as you are to fix it." (Ed.'s note: All quotations in this article are taken from the 72-page official transcript posted on the Supreme Court's Web site.)
Arguing for the government, Michael R. Dreeben, deputy solicitor general for the U.S. Department of Justice, countered that the court should move before Congress to fix an unsettled legal environment.
Calling Microsoft's position "radical," Dreeben described the current situation as one where no U.S. court gets to try to balance U.S. law with other countries' relevant laws. "If the data is stored overseas, we're just out of luck. We can't even ask a court for an order that would require its production," Dreeben said.
"No other court that has issued a written opinion since Microsoft has agreed with the Second Circuit. And the Second Circuit's decision has caused grave and immediate harm to the government's ability to
enforce federal criminal law," Dreeben argued.
He also urged the court not to wait for the CLOUD Act: "But as to the question about the CLOUD Act, as it's called, it has been introduced. It's not been marked up by any committee. It has not been voted on by any committee. And it certainly has not yet been enacted into law."
Predicting how justices will decide from the questions they ask in oral arguments is tricky, but there were some hints. Running through the justices in rough order from the liberal to the conservative end of the spectrum:
Justice Sonia Sotomayor asked Dreeben outright why the court shouldn't wait for Congress. "Why shouldn't we leave the status quo as it is and let Congress pass a bill in this new age?" Sotomayor also participated with several of the justices in lengthy exchanges to understand better how Microsoft would technically go about complying with an order to produce e-mails from a U.S. office that are stored in a datacenter in Ireland. At one point, Rosenkranz described the process as similar to dispatching a robot, saying, "If you sent a robot into a foreign land to seize evidence, it would certainly implicate foreign interests." Shortly after that description, Sotomayor joked, "I'm sorry...I guess my imagination is running wild."
Justice Ruth Bader Ginsburg offered similar thoughts on leaving action to Congress: "[In] 1986, no one ever heard of clouds. This kind of storage didn't exist. ... Wouldn't it be wiser just to say let's leave things as they are; if -- if Congress wants to regulate in this brave new world, it should do it?"
Justice Elena Kagan's questions were relatively technical, covering issues around whether judges could weigh other countries' laws in deciding on challenges to warrants, and discussing legislators' intent for specific provisions of the SCA.
Justice Stephen Breyer sought a short-circuit for the whole issue in trying to pin down whether Magistrate Court judges had authority to issue warrants for searches outside their geographic districts -- in this case, New York. "I suspect [that] it just can't be that easy, this case," Breyer said during a light moment in the arguments. Breyer also asked about the feasibility of a middle path involving reading the old statute to adapt to the current cloud environment.
Justice Anthony Kennedy wondered why the discussion about location wasn't broader. "Why should we have a binary choice between a focus on the location of the data and the location of the disclosure? Aren't there some other factors, where the owner of the e-mail lives or where the service provider has its headquarters?"
Justice Samuel Alito came down pretty heavily on the side of action -- the government's preferred position. "It would be good if Congress enacted legislation that modernized this, but in the interim, something has to be done," Alito said. Meanwhile, another question Alito asked established definitively that the nationality of the suspect in the case was not known, which may influence Kennedy's thinking based on his questions about locations. Alito also pressed Microsoft's Rosenkranz about what would happen in a case involving American citizens being investigated for crimes committed in the United States if their service providers store their e-mails outside the country.
Chief Justice John Roberts expressed deep reservations about service providers intentionally using the current legal standard to assist customers in avoiding U.S. investigators.
"There is nothing under your position that prevents Microsoft from storing United States communications, every one of them, either in Canada or Mexico or anywhere else, and then telling their customers: Don't worry if the government wants to get access to your communications; they won't be able to, unless they go through this MLAT [Mutual Legal Assistance Treaties] procedure, which is costly and time-consuming," he said. "Could you provide that service to your customers?"
In a give-and-take discussion, Rosenkranz assured Roberts that Microsoft's motives solely involved customer demands for minimizing latency, which he positioned as the sole reason for Microsoft's investment in half-billion-dollar datacenters all around the world. Roberts did not sound convinced, "Well, but you might gain customers if you can assure them, no matter what happens, the government won't be able to get access to their e-mails."
Justice Neil Gorsuch also seemed to stick to technical questions on subjects like the chain of activity in complying with a court order and the differences between subpoenas and warrants. At one point, Justice Breyer seemed to indicate to Dreeben that Gorsuch and others were "with you on this" but it was unclear exactly what Breyer was talking about.
Justice Clarence Thomas provided no clues as to his thinking during the oral arguments. He upheld his standard practice of asking no questions.
So the quick scorecard from this close read of the transcript is Sotomayor and Ginsburg leaning toward waiting for Congress, Alito and Roberts inclined to act, and the other five justices on the fence. Stay tuned for the decision in June.
Posted by Scott Bekker on February 28, 20180 comments
Expect to hear a lot about artificial intelligence (AI) at Microsoft Inspire, the company's annual July partner confab being held this year in Las Vegas.
Gavriella Schuster, corporate vice president for Microsoft One Commercial Partner (OCP), talked about Inspire in an interview posted this week on Vince Menzione's "Ultimate Guide to Partnering" webcast.
"The hottest topic at Inspire is probably going to be all about our data service and how to unlock that through artificial intelligence. That is clearly what all of our partners want to learn more about. It's what all of our customer engagements are about and every single one of our partners is buildings some sort of a data service, AI service, into their applications of the service that they deliver. That will be the theme of the whole event," Schuster told Menzione.
Schuster and her team at Microsoft made clear earlier this year that AI would be a major area of emphasis for partners in calendar year 2018.
On Jan. 24, Microsoft launched an AI Practice Development Playbook for partners. Based on detailed input from a dozen early-adopter partners and a survey of another 550 partners, the 144-page playbook goes through the basics of defining strategy, building a team, operationalizing a practice, going to market and closing deals.
Microsoft's intention with the playbook is to give its sizable partner base clear guidance on starting up AI practices, which would help Microsoft grab AI mindshare in what IDC calls a "Battle of AI Platforms" between Amazon, Google, IBM and Microsoft.
"Partners can build a roadmap that helps customers layer in sophisticated AI capabilities with minimal training," wrote Melissa Mulholland, cloud profitability lead for Microsoft, in the blog post introducing the playbook. The end game, she suggested, was for partners to "use AI technologies pragmatically to differentiate their current services, so they can re-engage customers with enhanced end-to-end systems that learn from data to deliver new insights and efficiencies."
In Schuster's interview this week, she suggested that, in keeping with the main idea of Inspire as a conference, hearing about AI successes and best practices would get partners thinking. "The more you hear about what partners are doing today and about what customers are doing, the more it sparks your imagination of what's possible and how to bring these different elements of the technology together," she said.
According to IDC analyst Steve White, that's probably the appropriate messaging for the current state of the AI opportunity. "AI is currently what cloud was a number of years ago," White said in an interview. "It's really, really interesting. It's going to be big in the future. Customers are going to be interested, but we haven't turned the corner yet on it. If you are an analytics partner, it should be an easy add. Those playbooks that Microsoft built are detailed. If you want to make that dive into it, they're a great place to start."
Posted by Scott Bekker on February 28, 20180 comments
A discrete cyber-espionage group operating on behalf of North Korea is responsible for a years-long series of cyberattacks, security researchers at FireEye said this week.
FireEye dubbed the group APT37 in its report, "APT37 (Reaper): The Overlooked North Korean Actor." The report connects APT37 to other attacks dating back to 2014, including the recent zero-day vulnerability CVE-2018-4878 that was disclosed on Feb. 1. Successful exploitation of that Adobe Flash Player vulnerability could allow an attacker to take control of an affected system.
FireEye's report ties that vulnerability to activities reported by other researchers, including Kaspersky Lab, which identified a group of attackers as ScarCruft, and Cisco's Talos unit, which identified the activities of a Group 123. The FireEye report goes further in pinpointing the group's origin as North Korea.
"We assess with high confidence that this activity is carried out on behalf of the North Korean government given malware development artifacts and targeting that aligns with North Korean state interests," FireEye wrote in the introduction to the report.
"We judge that APT37's primary mission is covert intelligence gathering in support of North Korea's strategic military, political and economic interests. This is based on consistent targeting of South Korean public and private entities and social engineering. APT37's recently expanded targeting scope also appears to have direct relevance to North Korea's strategic interests."
What's interesting about the report is that FireEye views APT37 as separate from the internationally isolated country's main suspected cyber-espionage and operations unit, which researchers call Lazarus. According to FireEye, the capabilities of APT37 are increasing, the unit's international scope of operations is expanding, and the group is likely to become another tool in North Korea's global cyber-operations arsenal.
Posted by Scott Bekker on February 21, 20180 comments
Ron Huddleston is joining cloud communications platform company Twilio as chief partners officer, the San Francisco-based company announced Monday.
Huddleston, who ran Microsoft's One Commercial Partner organization from its creation a year ago until going on what Microsoft officially described as an indefinite family leave two months ago, will be tasked with building out an ecosystem for ISVs, systems integrators and resellers at Twilio, a 10-year-old company that went public in June 2016.
"Ron's experience is unparalleled when it comes to building a thriving partner ecosystem and I look forward to him accelerating Twilio's momentum across all partner business models, geographies, and the enterprise opportunity," Twilio COO George Hu said in a statement. Huddleston helped build a developer-focused channel at Salesforce around AppExchange and previously held senior channel roles at Oracle.
"Twilio has the potential to revolutionize the communications industry in the same way cloud computing redefined the software industry. This is a massive opportunity for all types of partners to build new fast-growing businesses and continue to innovate for their customers across every industry," Huddleston said in the announcement.
The partner and developer evangelism role for Huddleston comes at a key time for Twilio, a 900-person company that is eager to show investors it is broadening its base of partners and customers. Twilio makes platform products that give developers APIs to allow them to embed communications technologies like voice, video, messaging and authentication into their own apps.
The company had a rough November, as investors punished the stock for the first full quarter of declining revenues from Uber. The ride-sharing app company decided last May to take more of the communications functionality of its apps either in-house or to use Twilio competitors in other geographies. Twilio's biggest customers are WhatsApp and Uber, which accounted for 6% and 5% of the company's revenues in the third quarter, respectively.
The danger of customer concentration is expected to be reflected in Twilio's fourth quarter results, which the company releases on Tuesday. Uber had accounted for 17 percent of Twilio revenues in Q4 2016, setting up a tough comparison.
At Microsoft, Gavriella Schuster replaced Huddleston as corporate vice president for One Commercial Partner in December, reporting to Judson Althoff, executive vice president for the Microsoft Worldwide Commercial Business.
Through
conversations with Althoff, CEO Satya Nadella and former COO Kevin Turner both before and after he joined the Microsoft Dynamics team in the summer of 2016, Huddleston helped define a new structure for Microsoft's massive channel operation. Starting with the creation of OCP in January 2017, Huddleston integrated developer evangelism much more tightly into partner operations and began work on
industry maps/solution maps/catalogs, which are
regional lists of go-to partners for different solution areas. The OCP structure also included a major
realignment of partner-facing job roles within Microsoft in the areas of build-with, sell-with and go-to-market.
Posted by Scott Bekker on February 12, 20180 comments
Technology solution provider Connection is joining the list of companies offering employee bonuses in the wake of the U.S. Tax Cuts and Jobs Act.
Connection, which was known as PC Connection from 1982 until late 2016, announced this week that it will pay a $1,000 cash bonus to each employee.
"We are pleased to be able to provide this special reward to our valued employees for their hard work and commitment to excellence," Timothy McGrath, CEO and President of the Merrimack, N.H.-based company said in a statement.
While the company's statement didn't say how many employees the company has, its last annual report filing with the U.S. Securities and Exchange Commission a year ago put the count at 2,500 people. Connection's statement also said the company is still evaluating provisions of the legislation, which was signed in December, but that it anticipates a beneficial impact.
Among dozens of companies that have announced one-time bonuses or pay hikes in relation to the tax law are American Airlines, Apple, AT&T, Bank of America, Best Buy, Disney, Walmart and Wells Fargo.
Posted by Scott Bekker on February 08, 20180 comments
If you think of Microsoft partners as organizations that consult on and implement Microsoft technology solutions, one of the largest organizations in the channel is Microsoft's own Enterprise Services arm, which includes Microsoft Consulting Services (MCS).
Microsoft generally keeps communications vague about Enterprise Services and MCS, due to the sensitive nature of its occasionally testy relationship with enterprise and federal government partners. Still, the company releases some broad outlines of the group's performance in every financial report, and last week's release was no exception.
"Enterprise Services revenue grew 5 percent, and 3 percent in constant currency, as growth in Premier Support Services and Microsoft Consulting Services was partially offset by declines in custom support agreements for Windows Server 2003," said Microsoft CFO Amy Hood during the call with financial analysts.
Details in Microsoft's 10-Q filing (.DOC) with the U.S. Securities and Exchange Commission indicated that the 5 percent amounted to $64 million, suggesting overall Enterprise Services revenues for the quarter were in the neighborhood of $1.3 billion.
What that tells us about actual MCS revenue is a little, but not a lot. We can infer that MCS revenues may be increasing at better than 5 percent to offset the custom support contracts. Meanwhile, it's hard to know how big a chunk of Enterprise Services revenues comes from MCS. Premier Support Services is a big business, and even a declining custom support agreement business is accounting for part of the revenue.
Looking ahead to Q3, Hood told analysts to expect a similar revenue growth rate for all of Enterprise Services in Q3 compared to Q2, with growth in Premier Support offsetting the Windows 2003 custom support agreement decline, and no mention of MCS as a major factor either up or down.
Microsoft's services are generally focused at the highest end, with the company claiming 75 percent of its engagements are with the Fortune 1000, and Microsoft often acts as a prime contractor, pulling partners into deals in various roles.
What are you seeing out there? Is MCS being more or less aggressive in competing with you for customer deals than you've seen in the past? Let me know at [email protected].
Posted by Scott Bekker on February 08, 20180 comments
Behind Microsoft's latest earnings results, which pleased financial analysts even if they didn't do much for the stock price, were a number of directional hints and other key details for Microsoft partners.
CEO Satya Nadella summarized the big picture for the quarter, which included a 12% increase in revenues to $28.9 billion and a 10% bump in operating income to $8.7 billion, this way: "The intelligent cloud and intelligent edge paradigm is fast becoming a reality. Azure growth accelerated. LinkedIn growth accelerated. Microsoft 365 and Dynamics 365 are driving our growth and transforming the workplace."
The solid results come despite the turmoil in the sales organization related to the massive, layoff-heavy reorganization of the Microsoft field during the last year. The upheaval was severe enough to merit a mention during the call for financial analysts by Microsoft CFO Amy Hood, who partly credited partners for soldiering through the transition.
"Our sales teams and channel partners delivered another quarter of outstanding commercial results even as we continue to work through our sales reorganization from July," Hood told the analysts Wednesday night.

"The intelligent cloud and intelligent edge paradigm is fast becoming a reality. Azure growth accelerated. LinkedIn growth accelerated. Microsoft 365 and Dynamics 365 are driving our growth and transforming the workplace."
Satya Nadella, CEO, Microsoft
For any partner that hasn't heard the cloud message that Microsoft has been delivering since, oh, 2006, Microsoft continued to push that flywheel during the analyst call, as well. Specific to Nadella's overview comment about accelerating Azure growth, Azure revenues were up 98%.
Following up on Nadella's high-profile commitment to reach a $20 billion annual run rate for commercial cloud revenue, which Microsoft hit in its last quarterly earnings period, Microsoft is now blasting past that number. Hood said commercial cloud revenue for the second quarter hit $5.3 billion, which amounted to a 56% year-over-year improvement.
Commercial revenues for Office 365, one of the most important business areas for the Microsoft channel, also continue to surge. Those revenues went up 41% in the quarter, attributable both to installed-base growth and upselling to the E3 and E5 workloads that Microsoft heavily encourages its partners to peddle.
Hood said Office 365 commercial seats were up 30% and, in response to an analyst question, said that Microsoft believes there is still a lot of growth opportunity with Office 365.
Meanwhile, Dynamics partners can expect pipeline check-in calls from their Microsoft partner management teams surrounding Hood's forecast for the next quarter. "We expect double-digit Dynamics revenue growth from the shift to Dynamics 365," she said.
The technical terms that break the surface in the earnings call provide a window into which technologies have strategic emphasis in Redmond. Nadella's technology namechecks this quarter included Microsoft 365, Cosmos DB, LinkedIn Sales Navigator, Dynamics 365 for Sales and Talent, the Profile Card, Resume Assistant, Azure Databricks, SQL Server for Linux, Azure IoT Central, Surface LTE, Teams and Cortana.
Posted by Scott Bekker on February 01, 20180 comments
Microsoft is close to delivering a handful of key Office 365 security enhancements, including an attack simulation tool to test end users' behavior, updates to the Office 365 Secure Score and message encryption improvements, according to the official Office 365 Roadmap.
The Attack Simulator for Office 365 Threat Intelligence has the potential to be a very useful proactive defense tool for Microsoft partners and IT administrators. Unveiled at Microsoft Ignite in September and set for an imminent public preview, the simulator is a new feature of Office 365 Threat Intelligence.
That Threat Intelligence service, launched last April, provides real-time security insights on global attack trends culled from what Microsoft describes as billions of data points from its global datacenters, Office clients and other sources.
According to the roadmap, the attack simulator "enables admins to send simulated attacks (10-15 different attack categories including phish, brute force password cracking, etc.) to their end users to determine how they respond to attacks and determine if the right policies are in place to help mitigate real attacks."
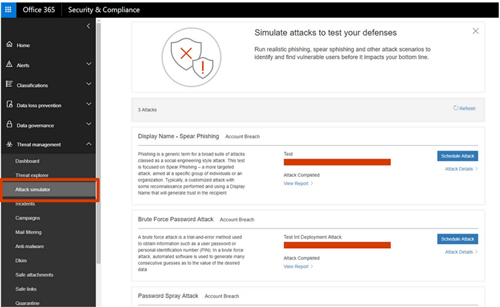 [Click on image for larger view.] The Attack Simulator for Office 365 Threat Intelligence will allow administrators to test users' password strength and phishing attack readiness, among other things. (Source: Microsoft)
[Click on image for larger view.] The Attack Simulator for Office 365 Threat Intelligence will allow administrators to test users' password strength and phishing attack readiness, among other things. (Source: Microsoft)
Also close are some additional features for the Office 365 Secure Score, which was originally came out a year ago to allow organizations to get a base security score from Microsoft based on dozens of factors in Office 365 covering user behaviors and security settings. It's like a credit score for an organization's cloud collaboration security posture.
Now Microsoft is adding an "Industry Average Score," displaying average scores that a company can compare to their own score. Microsoft is also testing an "Active Seat Average Score and Reporting Updates" feature for the Office 365 Secure Score. That will allow customers to compare their score against the average score for organizations with a similar number of Office 365 active seats. The update will also help organizations compare their own score between two different dates and offer the option to search a list of actions.
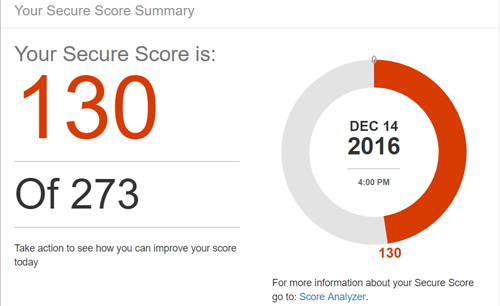 [Click on image for larger view.] Microsoft's original Office 365 Secure Score (pictured) became available a year ago. Microsoft is adding the ability for customers to compare their scores to like-size companies. (Source: Microsoft)
[Click on image for larger view.] Microsoft's original Office 365 Secure Score (pictured) became available a year ago. Microsoft is adding the ability for customers to compare their scores to like-size companies. (Source: Microsoft)
Microsoft is also fine-tuning the Office 365 Message Encryption capabilities it released in September. The feature was designed to make sharing of encrypted and rights-protected messages more seamless. However, the original release applied additional message restrictions, such as Do Not Forward. With the new version, administrators in the Admin Portal, or users in their Outlook client, can choose "encrypt only," without any other message restrictions.
In another change set to arrive shortly, Microsoft will add malicious link protection for end users sending e-mails within the same organization. Office 365 Advanced Threat Protection Safe Links for internal e-mails will include time-of-click protection and other functionality of Safe Links, Microsoft said. Slightly later in the quarter, Microsoft plans to introduce Office 365 Cloud App Security -- App Permission Alerts. The feature will allow administrators to create policies to be alerted when a user grants permission to an application to access Office 365 information.
All of the security features are currently in the "in development" section of Microsoft's Office 365 Roadmap page. Although many are supposed to be released very soon, the rollout for the Office 365 user base is staged and can take weeks or months.
Posted by Scott Bekker on January 31, 20180 comments