Report: Cryptomining Attacks Way Up in Q1 Even as Bitcoin Prices Fall
Cryptomining leapfrogged almost all other forms of malware detected in the first quarter of 2018, according to a new security report from Malwarebytes Labs.
"Cryptomining has just gone insane," said Adam Kujawa, director of Malwarebytes, in an interview about the report. "It's all over the place. We've never seen a mass migration to the use of one particular type of threat so fast by so much of the cybercrime community as we have seen with cryptominers."
Malwarebytes on Monday released "Cybercrime tactics and techniques: Q1 2018," the latest in its quarterly series of reports based on telemetry from its business and consumer products.
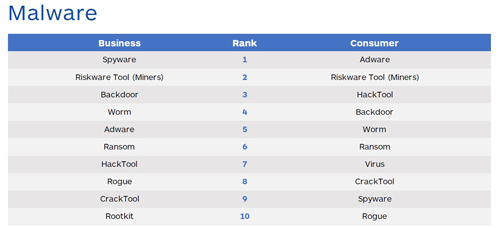 [Click on image for larger view.] Malwarebytes Labs' top 10 business and consumer malware detections in Q1 2018. (Source: "Cybercrime tactics and techniques: Q1 2018")
[Click on image for larger view.] Malwarebytes Labs' top 10 business and consumer malware detections in Q1 2018. (Source: "Cybercrime tactics and techniques: Q1 2018")
There are legitimate miners that get a user's consent before repurposing all or most of their CPU capacity toward mining for cryptocurrencies. Malwarebytes' report focuses on the other kinds -- malware-based miners that are often delivered via existing malware families and browser-based miners that hijack a victim's processor through drive-by attacks or malicious browser extensions.
The company found that cryptomining detections were way up in the quarter for consumers, with Android miners in particular surging to 40 times more detections this quarter than last. There was also a boom in March in Mac-based detections of malware-based miners, browser extensions and cryptomining apps, the company found.
For now, it's mainly a consumer problem. Business customers saw a 27 percent increase in cryptomining -- a significant jump to be sure, but nowhere near the levels on the consumer side.
This security report is a trailing indicator given that it covers the first three months of the year. Yet the cryptomining spike documented by Malwarebytes is tracking a little behind the price movement on the flagship cryptocurrency, Bitcoin, which had a recent peak in December but has been mostly falling from those highs over the last quarter.
Damages from cryptomining are squishy for businesses to calculate. A drive-by, browser-based attack, for example, can sometimes be stopped by simply shutting down the offending tab. Other types of cryptomining malware can be much more insidious.
How much damage is really done? There's lost productivity for sure, but Kujawa argues the malware delivery vectors that brought the cryptomining malware to systems will represent a lasting problem, even if cryptocurrency values don't rebound quickly and attackers lose interest in the attacks.
"A miner may only cause minimal damage, but any infection that you don't want to be on your system can install different stuff," he said. "The attacker sends a message to the miner: 'Hey install some ransomware for me, worm, go back to the old tricks.' It's like keeping your back door unlocked."
Posted by Scott Bekker on April 09, 2018