News
Top SMB Threats Include Ransomware and Windows Server 2012: Report
- By Gladys Rama
- April 04, 2024
Managed services providers (MSPs) that support SMBs have their hands full this year: The constellation of threats targeting their customer base is more varied and harder to detect than ever.
ConnectWise, an IT services firm that sells exclusively to channel partners, this week released the 2024 edition of its annual "MSP Threat Report" (available here with registration). It identifies trends within the cybersecurity landscape that are most relevant to SMBs -- and, by extension, the partners that they rely on to help keep their operations running smoothly.
Beware Zombie Windows Server 2012
Among other things, the report noted that SMBs still running Windows Server 2012, which officially fell out of support last October, could really use MSP intervention.
Unless these SMBs are enrolled in Microsoft's costly Extended Security Update (ESU) program, they are no longer receiving vital security updates for their Windows Server 2012 deployments, including patches -- leaving them vulnerable to security exploits. As the report put it, "[T]he next big Windows Server vulnerability that affects Server 2012 might never be patched, leaving affected servers vulnerable indefinitely."
Despite this, a not-insignificant proportion of SMBs are still running Windows Server 2012. According to data collected by ConnectWise through its security information and event management (SIEM) platform, Windows Server 2012 still accounted for about 14 percent of all Windows Server alerts, a fact it called "a significant security concern for all of us in 2024."
ConnectWise noted that SMBs are often hamstrung by a lack of in-house expertise, which is where MSPs come in. For SMB customers that are stuck running unsupported systems, MSPs can provide expert and dedicated cybersecurity vigilance; for those customers that pay Microsoft for an ESU contract, allowing them to continue receiving security updates, MSPs can manage their patch rollouts for them.
Ransomware Still the Low-Hanging Fruit of Cyberattacks
Recent history has been kind to ransomware attackers. A single ransomware attack can cost an organization anywhere between $1 to $10 million, the report noted, making it a $1 billion industry in 2023. Unsurprisingly, ransomware attacks have been on a steady incline; according to ConnectWise, the number of ransomware attacks it detected in 2023 nearly doubled year over year.
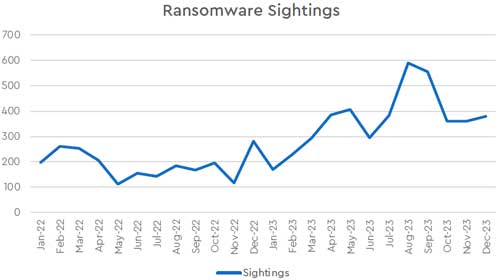 [Click on image for larger view.]
Figure 1. Ransomware activity by month from 2022 to 2023. (Source: ConnectWise, "2024 MSP Threat Report")
[Click on image for larger view.]
Figure 1. Ransomware activity by month from 2022 to 2023. (Source: ConnectWise, "2024 MSP Threat Report")
The company clocked about 4,400 distinct ransomware attacks last year, attributed to 57 separate groups (many of them new to the scene in 2023). However, just five of them accounted for more than half of all attacks. They are as follows:
- LockBit
- PLAY ransomware (aka PlayCrypt)
- BlackCat (aka ALPHV or Noberus)
- 8base
- Cl0p
ConnectWise observed ransomware attackers to increasingly favor tactics that help them avoid detection by traditional, single-layer security tools, making them difficult to avoid if you're an SMB with limited resources or an MSP with a security portfolio on the thinner side.
More Evasive Attack Methods Emerging
ConnectWise's researchers also identified the 10 most common methods used by attackers against its solutions in 2023. They are as follows:
| Exploitation for Client Execution |
Registry Run Keys/Startup Folder |
| Environmental Keying |
Valid Accounts |
| Obfuscated Files or Information |
System Binary Proxy Execution |
| Indirect Command Execution |
Process Injection |
| Windows Management Instrumentation |
Deobfuscate/Decode Files or Information |
Throughout 2023, ConnectWise detected 214 distinct methods, resulting in 280,000 attack attempts. The 10 listed above accounted for nearly half (45 percent) of those.
The report describes each method in detail, with recommended mitigation strategies for MSPs. Again, however, the overarching trend is that attackers are increasingly developing methods that can evade detection by endpoint detection and response (EDR) tools. That means MSPs can't rely on EDR tools by themselves to protect SMB clients; they need a layered solution, argued ConnectWise.
"[A] single solution is not enough and has the danger of creating a false sense of security," it said. "Building layers of defenses to include prevention (e.g., EDR), detection (e.g., SIEM), and 24/7 monitoring (e.g., managed security operations center [SOC]) creates a maze for attackers to navigate instead of a wall to scale."
Besides those solutions (of which ConnectWise is naturally a provider), the report also recommends that MSPs implement strategies like zero-trust security, multifactor authentication, non-repeating passwords and robust permission policies.