SophosLabs: A Quarter of Malware Using TLS
The industrywide push in recent years toward encrypting Web traffic isn't just for good guys.
Encryption has always been neutral, as useful to bad actors for hiding nefarious activity as it is for legitimate users trying to protect their data from those trying to steal it.
New research from SophosLabs documents how widespread the use of HTTPS connections is becoming in malware circles, especially for communicating back to command-and-control servers (C2).
SophosLabs on Tuesday reported on a representative sampling of malware analyses the research team has conducted over the past six months.
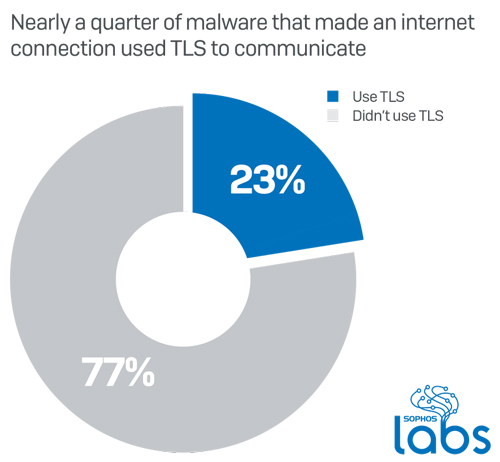
"Out of all the malware that made some kind of network connection during their infection process, about 23% communicated over HTTPS, either to send or receive data from the C2, or during installation when they may use HTTPS to conceal the fact that they are retrieving malicious payloads or components," SophosLabs threat researcher Luca Nagy wrote in the blog post describing the research.
Not all types of malware communicate equally over TLS. Information-stealing trojans made up only 16 percent of the samples SophosLabs tested during the six-month period, but of those, 44 percent used TLS over standard HTTPS ports. Ransomware, which does its damage in other ways, was less likely to use encryption when calling home.
Sophos released the research Tuesday in conjunction with the launch of a new firewall, which features more advanced SSL inspection, including support for TLS 1.3 without requiring downgrading, new policy tools and performance improvements. More detail on XG Firewall v18 is available here.
Posted by Scott Bekker on February 18, 2020