Microsoft Cloud a 'Tempting Target' for Attacks
A new Microsoft security report released this week quantifies a longstanding concern about big cloud services, namely that hyperscale clouds appeal to attackers like banks attract robbers.
After all, the Microsofts, Amazon Web Services and Googles of the world are increasingly where the users and data are. The bet by customers and the industry on big clouds is that in the arms race between attackers and defenders, the risks of putting all the data under only a few vendors' control can be outweighed by the high-quality people and processes the hyperscale vendors will be able to afford.
The latest data points on the question come from the Microsoft Security Intelligence Report (SIR) released on Thursday. Version 22 of the somewhat sporadic report has an increased focus on cloud, and Microsoft comes right out and admits the obvious point that its cloud makes an appealing target.
"Consumer and Enterprise Microsoft accounts are a tempting target for attackers, and the frequency and sophistication of attacks on cloud-based accounts are accelerating," Microsoft's report states.
Just how attractive is made clear in the report, which relies on telemetry data from various Microsoft products and services, such as its monthly scanning of 400 billion e-mails for phishing and malware, processing of 450 billion authentications, and executing of more than 18 billion Web page checks.
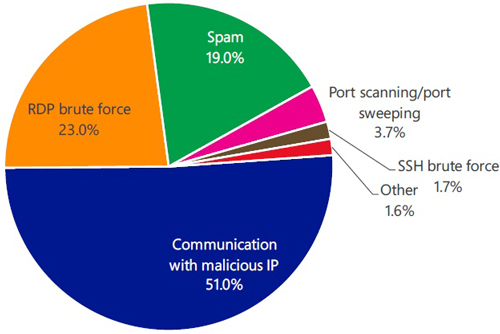 [Click on image for larger view.] Outbound attacks detected by the Azure Security Center in Q1 of 2017. (Source: Microsoft)
[Click on image for larger view.] Outbound attacks detected by the Azure Security Center in Q1 of 2017. (Source: Microsoft)
"The Identity Security and Protection team has seen a 300 percent increase in user accounts attacked over the past year," the report notes in language indicating that it is referring to successful attacks.
No matter how effective Microsoft's defenses are, the report contends that enterprise and end user security practices need to improve. "A large majority of these compromises are the result of weak, guessable passwords and poor password management, followed by targeted phishing attacks and breaches of third-party services," the report states.
Attacks are flooding in from bad sectors of the Internet. "The number of Microsoft account sign-ins attempted from malicious IP addresses has increased by 44 percent from 1Q16 to 1Q17," according to the report.
The report does not break out specific numbers, only percentages. It also doesn't quantify how many successful attacks and unsuccessful attempts were aimed at business versus consumer accounts in the Microsoft cloud.
In addition to targeting the digital assets or identities of targeted accounts, a portion of the attacks involve something Microsoft has referred to in previous editions of its SIR as "cloud service weaponization." That involves attackers compromising accounts in order to take over Azure-based virtual machines, which can then be redirected to other nefarious purposes, similar in concept to botnets.
According to Microsoft Azure Security Center data cited in the report, the three most common types of outbound attack traffic that compromised Azure-based virtual machines attempt to send are communications with malicious IPs, RDP brute force and spam.
On the other side of the ledger, Microsoft's report details various Microsoft products and services that can help customers and end users combat attackers, such as Windows Hello for Business, Credential Guard, Microsoft Azure Active Directory Identity Protection and Azure Multi-Factor Authentication.
Posted by Scott Bekker on August 18, 2017