In-Depth
Secunia Report Highlights Critical Importance of Non-Microsoft Patches
WEB EXCLUSIVE: The count of overall vulnerabilities went up by 18 percent from 2013 to 2014, led by a surge in browser vulnerabilities. The Windows OSes saw a drop in new vulnerabilities.
- By Scott Bekker
- March 25, 2015
Microsoft remains the 800-pound gorilla of PC software, but when it comes to securing most PCs against vulnerabilities, those high-profile monthly Microsoft patches are a surprisingly small part of the job, a new study makes clear.
Vulnerability management vendor Secunia on Wednesday released its annual "Secunia Vulnerability Review." Overall findings were that the number of new vulnerabilities reported in 2014 went up by 18 percent compared to 2013. Newly reported vulnerabilities totaled 15,435 in 3,870 applications from 500 publishers, Secunia said. Among those thousands of new vulnerabilities were 25 zero-day vulnerabilities, which are security flaws that are already being exploited in the wild when a vendor publishes a security advisory about them. That figure is up from 14 zero-days in 2013.
"There is a general increase we're seeing in the number of vulnerabilities," said Kasper Lindgaard, director of research and security at Secunia, in a telephone interview. "It's not a new world, but it's definitely a changed world. More and more vulnerabilities are discovered every single year. Companies need to step up [their patching efforts]."
A theme emerging from Secunia's reports over the last several years is that Microsoft software dominates on individual Windows desktops but accounts for a comparatively small percentage of the vulnerabilities. In other words, the majority of the dangerous problems on Windows PCs come from the non-Microsoft software.
As part of its methodology, Secunia creates a hypothetical endpoint called the Top 50 Portfolio. This construct is a PC running Windows 7 and 50 of the most common products on PCs, a list assembled from anonymous scans of millions of private computers running the Secunia Personal Software Inspector. Secunia's approach is similar to the "basket of goods" economists use to estimate inflation.
The Top 50 Portfolio is dominated by Microsoft software -- Windows 7, Internet Explorer, the .NET Framework, Silverlight, Windows Defender, Windows Media Player, the Office applications, et cetera. According to Secunia, Microsoft applications account for 69 percent of the applications in the Top 50 Portfolio. However, within that portfolio -- a standard PC -- non-Microsoft software accounts for 77 percent of the vulnerabilities.
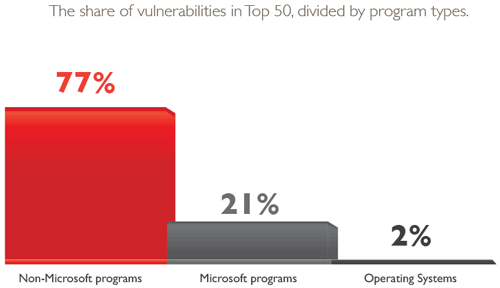 Windows and Microsoft applications make up 69 percent of the top 50 applications on PCs measured by Secunia, but account for a much smaller proportion of vulnerabilities. (Source: "Secunia Vulnerability Review 2015.")
Windows and Microsoft applications make up 69 percent of the top 50 applications on PCs measured by Secunia, but account for a much smaller proportion of vulnerabilities. (Source: "Secunia Vulnerability Review 2015.")
Windows Flaws
Vulnerabilities in the Windows operating system itself accounted for a little over 2 percent of the flaws in the Top 50 Portfolio. In fact, Windows OS flaws bucked the overall trend and fell in number in 2014. Newly discovered vulnerabilities dropped from 2013 to 2014 for Windows 8 (156 to 105), Windows 7 (102 to 33) and Vista (102 to 30).
Lindgaard said it's hard to pinpoint why the 2013 count for Windows vulnerabilities was so much higher.
"There are probably a number of factors in play -- one likely explanation is that it is a common condition in the security industry that security researchers shift their research time, focus and scrutiny from one program or product type to another, thereby resulting in more vulnerabilities being discovered in a program of choice. The high number of vulnerabilities in Windows 8 specifically [156] in 2013, was due to the fact that Windows 8 has Adobe Flash Player integrated into Internet Explorer. This integration was responsible for a third of the vulnerabilities [55] detected in that particular Windows operating system," Lindgaard said.
Several other operating systems actually saw more vulnerabilities in their platforms than the flavors of Windows, according to Secunia's numbers.
| Operating System Vulnerabilities in 2014 |
| Operating System |
Vulnerabilities |
| Oracle Solaris |
483 |
| Gentoo Linux |
350 |
| Apple Macintosh OS X |
147 |
| Windows 8 |
105 |
| Windows 7 |
33 |
| Windows Vista |
30 |
| Windows XP * |
5 |
* Support, and vulnerability reports, ended April 8
Source: "Secunia Vulnerability Review 2015"
|
Other Microsoft applications in the Top 50 Portfolio, however, saw a spike in vulnerabilities -- up 45 percent over the prior year. IE was the biggest offender at 289 vulnerabilities. Word was second-highest in the group with 13 flaws.
Browsers: Target of the Year
As to where the attention has turned, that answer is easy to pinpoint -- the browser. Browser flaws were up 42 percent in 2014 to 1,035 in the top five browsers. Google Chrome drove almost half of that activity. With 504 newly discovered vulnerabilities, Google Chrome tops Secunia's list for the core product with the most vulnerabilities in 2014.
Although it surged way past perennial security whipping boy IE, Lindgaard cautioned that Google's bumper crop of vulnerabilities isn't necessarily a bad sign. As evidenced by Google's recent brouhaha with Microsoft over publicly reporting new vulnerabilities after a grace period whether or not they're patched, Google has placed more emphasis on security lately.
"The funny thing about Google Chrome is that the majority of the vulnerabilities being patched, a big part of it, is Google finding the vulnerabilities themselves. They're also paying a fair amount of money [in bug bounties]," Lindgaard said. He noted that many of Google's advisories in 2014 would include a bug bounty patch and bundle in a large number of internally discovered flaws.
| The 20 Core Products with the Most Vulnerabilities in 2014 |
| Rank |
Product |
Vulnerabilities |
| 1 |
Google Chrome |
504 |
| 2 |
Oracle Solaris |
483 |
| 3 |
Gentoo Linux |
350 |
| 4 |
Microsoft Internet Explorer |
289 |
| 5 |
Avant Browser |
259 |
| 6 |
IBM Tivoli Endpoint Manager |
258 |
| 7 |
IBM Tivoli Storage Productivity Center |
231 |
| 8 |
IBM Websphere Application Server |
210 |
| 9 |
IBM Domino |
177 |
| 10 |
IBM Notes |
174 |
| 11 |
Mozilla Firefox |
171 |
| 12 |
X.ORG XSERVER |
152 |
| 13 |
Apple Macintosh OS X |
147 |
| 14 |
IBM Tivoli Composite Application Manager for Transactions |
136 |
| 15 |
VMware vCenter Server |
124 |
| 16 |
IBM Tivoli Application Dependency Discovery Manager |
122 |
| 17 |
Oracle Java |
119 |
| 18 |
VMware vSphere Update Manager |
111 |
| 19 |
IBM Websphere Portal |
107 |
| 20 |
Microsoft Windows 8 |
105 |
Source: "Secunia Vulnerability Review 2015"
|
One promising trend in the overall vulnerability landscape is completely reversed in the Top 50 Portfolio. The severity of vulnerabilities seems to be getting lower among all applications. The percentage of the overall field of 15,435 vulnerabilities that rated as either highly critical or extremely critical was just over 11 percent. Zero in on the 1,348 vulnerabilities in the Top 50 Portfolio, though, and the percentage of flaws that are highly critical or extremely critical is nearly 75 percent.
"In the Top 50, it's mostly Windows 7, the Office products, browsers and Flash. The most common attack vector in those applications is e-mail load. It's fast, it's luring you to a Web site. Most of the applications in the Top 50 actually accommodate for the remote attack vector," Lindgaard said.
Another trend Secunia found that is unequivocally promising is an increase in the percentage of vulnerabilities for which a patch is available on the day of disclosure.
For all vulnerabilities in all products, 83 percent have patches on the first day, and the figure is 87 percent within the Top 50 Portfolio, Secunia found. The 83 percent figure represents a lot of progress from the 50 percent that Secunia recorded in 2009.
"We definitely see a more mature security landscape now than five years ago," Lindgaard said. "Vendors have security teams, bounty programs. They used to put [third-party vulnerability reports] on waiting lists."
That said, there's very little daylight between vendor performance on Day 1 and Day 30. Of vendors who haven't patched a vulnerability on the day of disclosure, very few get around to it within a month. The day of disclosure patch rate is 83.1 percent. The 30-day patch rate is barely any higher at 84.3 percent.
The amount of Microsoft software on a standard system means Microsoft's Patch Tuesday continues to be incredibly important for IT departments around the world. If Microsoft were to slack off, new vulnerabilities would surely proliferate. But Secunia's report underscores how much larger the job of keeping systems patched is than simply tracking Microsoft's advisories.
According to a section of the report about the Top 50 Portfolio: "End users and organizations cannot manage security by focusing on patching Microsoft applications and operating systems alone. If they do that, they are only protecting their computers and IT infrastructures from 23.1 percent -- less than a quarter -- of the total risk posed by vulnerabilities."
A PDF of the 24-page "Secunia Vulnerability Review 2015" is available here.