In-Depth
Security Lockdown Guide: How To Fight the Next Generation of Black Hats
The proliferation of cloud services, mobile devices and Big Data presents a radically altered attack surface for customer IT assets. The Black Hats have adapted. Have you?
- By Scott Bekker
- December 08, 2014
Five years ago, the security baseline was pretty similar to what it had been five or even 10 years before that. If you had a firewall, if you had good patch management processes, if you had server and client antivirus, if you had a VPN set up, you were probably going to prevent the bulk of potential issues. If you look at a classic model of 20 percent of tools preventing 80 percent of the problems, you could make a case for that toolset. You had basically defended the organization from charges of security negligence.
In the last few years, ongoing seismic shocks in the IT industry are reshaping the attack surface for corporate data. A new generation of attackers is adapting to the changes hourly, yet the attitudes of many in charge of data defense are half a decade or more out of date.
Blown Assumptions
What are some of the outdated assumptions that those responsible for securing organizations need to root out of their thinking? RCP put the question to Kenneth Schneider, vice president of technology strategy at security giant Symantec Corp. Schneider laid out a few of the most dangerous old chestnuts of wisdom.
"Knowledge workers are using some well-behaved PC that sits in one place, where they're interacting with it and creating sensitive information," Schneider says in providing one old assumption. "Obviously, mobility has blown that all out."
Another is that Windows is your attack surface. "The whole monoculture of Windows was prevalent; now you have the diversity of devices," he says. (For proof, consider Microsoft COO Kevin Turner's assertion over the summer that Microsoft has a 14 percent share of the total device market.)
"There was a glass tower where your key information was locked. You had a pretty good moat around the whole thing," Schneider says of the old days. "Now we're seeing merged infrastructures. Now it's not just servers running on physical infrastructure: It's now being run in private cloud environments; it's being moved to public cloud SaaS [Software as a Service]."
It's a brave new world, what with bring-your-own-device (BYOD) and non-BYOD mobility, the employees working permanently outside of official corporate offices, the constant Wi-Fi connectivity both in company-controlled networks and public networks, the hundreds of sanctioned and non-sanctioned cloud apps employees use to conduct work-related business, Internet of Things (IoT) devices and new breeds of attackers.
Schneider says security now requires an entirely different mindset: "The key asset that security has to protect is information. It's not about protecting systems."
Three Types of Attackers
In any adversarial system, be it business competition, legal settings or sports contests, the evolution of one side has to drive evolution on the other side. The zero-sum game of attacking and defending digital data is no exception. To understand changing rules on the defending side, it's necessary to look at the changing actions and players on the offensive side.
"If you go back 10 years, it was mostly financially motivated spam and phishing attacks, and spam was really taking off," says Schneider. "The thing that's changed is it's not just somebody trying to prove how smart they are or make money -- the new styles of threat are about cybersecurity attacks trying to steal specific kinds of intellectual property or secrets," Schneider asserts.
 "You've got to make yourself a hard target. At the moment, for the bad guys, it's shooting fish in a barrel. If you're a harder target than the next guy, they will just move on."
"You've got to make yourself a hard target. At the moment, for the bad guys, it's shooting fish in a barrel. If you're a harder target than the next guy, they will just move on."
Stu Sjouwerman, CEO, KnowBe4 LLC
Stu Sjouwerman, CEO of KnowBe4 LLC, a security training startup, also believes attacks have become substantially more serious. "Management needs to understand that this is a whole different environment compared to five years ago."
Driving attacks are three primary trends: professionalization of cybercrime, the big-time emergence of script-kiddie tools and government-backed snooping.
"Cybercrime has gone pro. That's the main thing that people need to understand," says Sjouwerman, sounding a theme common among security professionals.
"There is a well-developed, fully operational criminal underground that has specializations," Sjouwerman explains. "There are escrow services for criminals by criminals that allow criminals to do business with one another. There's a whole supply chain of people that are specializing in the different parts of a phishing attack. There's people specialized in hacking accounts and stealing data to sell it. There's people who are specialized in merge/purge and creating databases of e-mail addresses to send these attacks to. Then there's another group that's specializing in putting a quality phishing attack together that's real enough to get people to click on it. Then there are people that specialize in pulling together botnets. There are project managers putting together campaigns. Then there are the people that finance it."
Being a hacker, in the attacker sense, once meant that a person had a certain amount of technical skill that those in the security industry couldn't help but respect. The emergence of extremely powerful and easy to use tools has led to a large group of attackers known as script kiddies, who need barely any technical skill to do serious damage. Some common penetration testing tools often used by white hat hackers to legitimately test system vulnerabilities illustrate how far these tools have come.
Freely available tools include Kali Linux, a pentest-optimized distribution of Linux that can be booted from a DVD or a USB stick and comes pre-loaded with dozens of tools for attacking everything from wireless routers to desktops and servers to Android phones. One popular tool included with Kali Linux is Metasploit, an exploit framework that can be run with a GUI. Metasploit allows a user to attack a system by picking exploits, payloads and post-attack actions from dropdown menus. Those exploits are updated almost as quickly as software vendors reveal new security flaws. The upshot -- a newbie can execute highly sophisticated attacks against the most recently reported vulnerabilities.
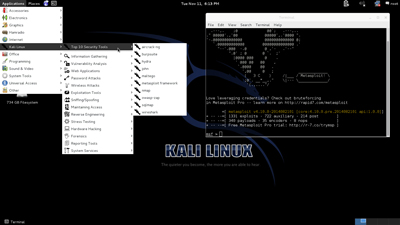 [Click on image for larger view.]
Kali Linux is a free penetration testing-focused distribution of Linux that's preloaded with dozens of hacking tools. Pictured is a Kali Linux desktop showing the Top 10 Security Tools menu. Metasploit, a framework for exploiting vulnerabilities, is open in the Terminal window. Powerful, easy-to-use tools like these are making so-called script kiddies much more dangerous. But they also make it easy for organizations to test and harden their own networks.
[Click on image for larger view.]
Kali Linux is a free penetration testing-focused distribution of Linux that's preloaded with dozens of hacking tools. Pictured is a Kali Linux desktop showing the Top 10 Security Tools menu. Metasploit, a framework for exploiting vulnerabilities, is open in the Terminal window. Powerful, easy-to-use tools like these are making so-called script kiddies much more dangerous. But they also make it easy for organizations to test and harden their own networks.
On the opposite end of the sophistication scale from the script kiddies are the government snoops. The early part of 2013 brought a lot of accusations about Chinese military-backed penetration of U.S.-based companies and infrastructures. That news, of course, was eclipsed by the revelations of former U.S. National Security Agency contractor Edward Snowden about the aggressive data acquisition and penetration efforts of the U.S. government.
New Rules for Securing Information
Conversations with about a dozen security leaders covered a broad array of potential adjustments for the emerging threat environment, but a few common themes surfaced.
1. Concentrate on the User
"The user is actually the new perimeter," alleges Jonathan Trull, chief information security officer at Qualys Inc., a vulnerability management company. The user is the one with the mobile device accessing corporate data from well outside the corporate firewall. The user is the one logging into business-focused cloud services from work and personal devices, and logging onto personal cloud services from work devices. The user is the one going to social media applications both as part of their job and for personal reasons.
Here's the thing about that -- users make for a terribly insecure perimeter.
"It's terrifyingly easy to get users to provide their passwords," says Chris Webber, security strategist at Centrify Corp., a company focused on helping companies provide their users with secure access to cloud apps.
"The user ultimately is the weak link in IT security," adds Sjouwerman, who is building a business on that problem, attempting to educate users about drive-by-downloads, spear phishing and other ways they can inadvertently endanger their employers. "The whole idea is that they understand that the Internet is pretty bad. It's the Wild Wild Web. It's getting worse, it's not getting any better. I think investing in security awareness training is the best bang for your buck at the moment."
 "One of the first things that an attacker is going to do, black hat or white hat, is profile the company."
"One of the first things that an attacker is going to do, black hat or white hat, is profile the company."
Jonathan Trull, Chief Information Security Officer, Qualys Inc.
That education also needs to extend to social media usage, says Qualys' Trull. "We train as part of your security awareness that one of the first things that an attacker is going to do, black hat or white hat, is profile the company. I'm going to start looking at who is on the different social media sites I can get access to and look at the things they're posting. Engineers trying to solve a problem will post a question to forums. I'm having trouble with a certain version of Oracle and I'm trying to do x, y and z."
Another thing about users today is that IT can no longer imperiously refuse them services, even for solid security reasons. "One of the things that we learned early on was something that was very fundamental to our strategy," explains Mike Raggo, security evangelist at MobileIron. "The more IT says no, the less secure the environment becomes. A lot of the services that we want to provide to users on these mobile devices can be delivered in a very secure manner. But if we lock things down too much, they're going to find a way around it. We call that shadow IT."
2. Work with the Cloud
The blurring of the network edge isn't just happening with mobile devices. The edge is also blurring into the cloud -- another area that IT departments and companies' solution provider partners don't control. Forward-leaning customers and partners are taking a few steps, though.
One step is to figure out which cloud apps employees are actually using. Speaking to Raggo's point about employees finding a way to get their work done, auditing which cloud apps are in use can be an eye-opening experience.
The most recent quarterly "Cloud Adoption and Risk Report" (registration required) from cloud security vendor Skyhigh Networks provides a taste. Skyhigh discovers cloud services in use by a company's employees. Using anonymized data across its customer and prospect base, Skyhigh determined that in the second quarter of this year, companies used an average of 738 discrete cloud services. At the same time, those IT departments were aware of an average of only 30 cloud services being in use at their organizations.
Frank Cabri, vice president of marketing at a different cloud security company, Skyfence Networks Ltd, has names for the two types of cloud apps. "Sanctioned" apps are the ones the IT department knows about and approves. They might include Microsoft Office 365 or Salesforce.com or Amazon Web Services (AWS). "Unsanctioned" apps are the ones the business groups or individual users installed without any IT involvement. They could be some of the same apps from the sanctioned list done on the sly or a free file sharing service set up to meet a departmental business need, or the Twitter, Evernote or Yahoo Mail accounts of individual users, accessed on occasion from the company network.
If knowing what cloud apps are in use is step one, helping users safely manage their passwords is the huge step two.
"We know that users are using the same password for their internal business applications as they do for their social media applications," Qualys' Trull says.
Centrify's Webber notes that compromised user passwords are the low-hanging fruit of the IT world. "Bad guys know no matter where folks are accessing data from or where the data lives, traditional perimeter defenses are getting better and better. Why try to smash down that vault door and be an unauthorized [intruder]? It's much better to pretend to be someone who is authorized and walk right in," Webber says. Centrify's software lets companies offer employees a menu of more than 2,500 cloud apps. Those users can securely access the apps without ever creating or entering an individual password.
Webber and others mentioned the importance of two-factor authentication technologies to ensure identity in certain scenarios -- such as when a user is logging in from another country on an unknown device. Security vendor AVG Technologies, a major provider of remote monitoring and management software, recently announced a partnership with Centrify Corp. to integrate that technology into its tools for managed services providers (MSPs). Another MSP tools provider, Kaseya Ltd., has recently branched out to provide a two-factor authentication solution, as well.
Finally, encryption is a solution getting more and more attention for organizations intent on securing their data in the cloud. "Data encryption and everything that goes with that are going to be more and more important. As data is moving from your servers to clouds to home PCs, I think encryption is going to be key," says Qualys' Trull.
3. Revisit (and Revise) the Basics
Even as different types of attacks proliferate, the old ones don't go away. And like a struggling sports team, many companies are failing on the fundamentals.
"Unfortunately, still, the majority of companies aren't even doing the basics well, [even when those basics are defined as the old fundamentals from five or 10 years ago]. If you talk about small businesses, oftentimes they struggle to have someone on their staff to have the kind of expertise to even do security," says Trull.
Case in point is the long overhang of organizations still running unpatched and unsupported Windows XP on Internet-facing systems.
 "Sometimes you're under attack for days, weeks or even months. You think everything is hunky dory, everything is great. In reality, we don't know what we don't know."
"Sometimes you're under attack for days, weeks or even months. You think everything is hunky dory, everything is great. In reality, we don't know what we don't know."
Dror Nadler, Senior Vice President, Sales and Strategic Alliances, Cellrox
Another commonly missed basic, according to Rob Juncker, vice president of engineering at LANDesk Software: "Take administrator rights away from your users. Most of them don't need it, but a lot of them still have it."
Even companies that have the firewall in place and the patch management process humming need to make some adjustments, Juncker says.
"In the past we talked about firewalls doing things like just blocking incoming communications over certain ports that are known bad. Nowadays when we talk to customers, we want to make sure that they're blocking known bad outgoing communications like SMB, IRC or very high number ports," Juncker says. "Most people set their firewall rules up and then they don't monitor them. Make sure that you're actively gathering those logs, and looking for changes in the overall activity. As mundane as it sounds, you probably need to block more with your firewalls."
Often companies aren't keeping up with developments in the patching world either, says Juncker, who joined LANDesk through the acquisition of the Shavlik patch management unit from VMware Inc. "I think a lot of us focus on Microsoft products. That's where a lot of the exploits used to be. Now they lead out with Java, they lead out with Adobe. The operating system isn't enough anymore. Making sure that you have a patch process that emphasizes not just servers, but make sure you get the endpoints."
Another key patching development that many organizations have missed is the general increase in patches for zero-day exploits. According to Juncker, organizations need a separate, accelerated process to update systems threatened by zero-day exploits than they use for regular vulnerability patches.
"With Microsoft Patch Tuesday, we see most people strive for 90 percent of their security patches applied within a week and a half. For zero days, it's a totally different story. As soon as we release that patch, someone will pick up that patch, test it the next day and do some basic surface testing. After that's done they start pushing it out to critical systems, with awareness of how you would handle breakage. They take a little more risk on the upgrade with that testing," Juncker notes.
4. Assume Attackers Are Already In
More and more often, security experts are counseling customers to work from the assumption that their networks are already compromised to some degree.
"At this point, you can no longer assume that you can keep the bad guys out. You basically have to take the premise that the bad guys are already in, and how do I detect the breach?" says Sjouwerman. "If the bad guys really want to get in, they're already in. There are so many existing zero-day vulnerabilities. It's the 'bigger hammer' concept. If you have a hammer big enough, you can get into anything."
Dror Nadler, senior vice president of sales and strategic alliances at Cellrox, a mobile device protection company, says that many recent incidents involved attackers who were parked on the network.
"Sometimes you're under attack for days, weeks or even months. You think everything is hunky dory, everything is great. In reality, we don't know what we don't know. Getting some predictability and making some analysis around patterns that you are expecting to see in your network and comparing it day by day. Based on that you know when there's something fishy. You may not know what's wrong, but you know something is wrong," Nadler says.
LANDesk's Juncker concurs: "Baseline, baseline, baseline. Malware will no longer jump out at you and say I'm on your network."
5. Prioritize Your Information
Assuming the attackers are in, the game becomes about limiting the damage.
"They've gone past my defenses. What do I do to keep them from exfiltrating the crown jewels? Now you're talking about things like breach-detection software. You're talking about your layering, your defense in-depth." Sjouwerman says.
For layering and defense in-depth to be effective, it has to be planned before the attackers are in the network. Those approaches require thinking about how to place corporate information so that important information is very difficult to get at, while less important information is less protected. In other words, prioritizing.
Very little prioritizing has been happening on most networks to date, contends Ian Trump, security lead at LogicNow Ltd., the IT services management business created from part of GFI Software in September.
 "He who defends everything, defends nothing. You can overwhelm yourself with the data. It's really about understanding the core business function and protecting it with those different layers."
"He who defends everything, defends nothing. You can overwhelm yourself with the data. It's really about understanding the core business function and protecting it with those different layers."
Ian Trump, Security Lead, LogicNow Ltd.
"It's been ridiculous what we've thrown on the network," Trump says, ticking off new elements. "HVAC, post office machine, a zillion different devices with different operating systems. Everything has a Web server built into it. We also put the phone system on the same network. Then somebody said, 'You know what? We could also process your credit cards over the same network.'"
Trump says organizations first have to understand what data makes them money. Then they need to separate the must-haves from the cool-to-haves. "If it has anything to do with money, think twice about putting it on the network. The cybercriminals want your money, that's it. On a general-purpose network, you've just given them hundreds of different ways to get it," he says.
"He who defends everything, defends nothing," Trump says. "You can overwhelm yourself with the data. It's really about understanding the core business function and protecting it with those different layers."
Escaping the Bear
Symantec's Schneider is unequivocal about the new security landscape. It's all the old threats, plus many new ones. "The world has gotten harder for any company trying to secure themselves," he says.
There's one encouraging note in this symphony of pain. It goes to the tongue-in-cheek anecdote common among hikers: You don't have to be faster than the bear. You only need to be faster than the slowest person in your group.
With so few companies handling their own security competently in this evolving environment, you don't have to do everything right as long as you get most of it done. Says Sjouwerman, "You've got to make yourself a hard target. At the moment, for the bad guys, it's shooting fish in a barrel. If you're a harder target than the next guy, they will just move on."