News
Azure AD Outage Linked to Multifactor Authentication Issues
- By Kurt Mackie
- October 18, 2019
An Azure Active Directory outage that lasted for about 2.5 hours in the morning of Friday, Oct. 18, was caused by multifactor authentication (MFA) challenges not working, according to Microsoft.
MFA is a process in which users validate their identity via another means besides a password. MFA is part of the Azure AD service, which is used for signing into various applications. The outage on Friday blocked customers from accessing those applications.
An Azure Status page message from Microsoft (at about 9:40 a.m. PST on Friday) suggested that the problem had been resolved. Here's that message:
Information Authentication issues with Azure MFA
Customers in North America experienced issues with completing MFA challenges from approximately 6:30 AM PST until 9:00 AM PST.
As of now, Our telemetry and customers feedback indicates the issue is mitigated.
We are closely monitoring the situation to ensure this does not recur.
Earlier, the Azure Status page had described the issue as being under investigation, where Microsoft suspected the issue was associated with "config changes, recent patches and networking issues." Here's how it was expressed:
Information Authentication issues with Azure MFA
We are aware that customers in North America are experiencing issues with completing MFA challenges. This issue started at approximately 6:30 AM PST and is ongoing. We are aware of how critical this is to your business and security. We are actively investigating the issue as our absolute top priority and working for the fastest possible resolution.
At this point, we are investigating potential root causes including but not limited to config changes, recent patches and networking issues, but we have not isolated any root cause or mitigation yet.
We will send out update within the next 60 minutes or as events warrant.
An Azure outage map by Downdetector.com showed that an outage mostly hit the United States. The map is based on complaints, which spanned a two-hour time period. Those complaints are generalized under the Azure "cloud services" label.
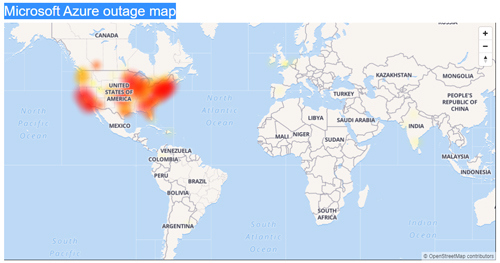 [Click on image for larger view.] Heat map of Azure outage on Oct. 18 based on complaints. (Source: Downdetector.com)
[Click on image for larger view.] Heat map of Azure outage on Oct. 18 based on complaints. (Source: Downdetector.com)
Apparently, Microsoft thought the issue early on was confined to signing into the Azure Admin Center portal. However, early reports by individuals on Twitter typically stated that the problem wasn't just with using MFA to access the Azure Admin Center portal but also Office 365. One person commented that the Microsoft 365 Service Health portal "incorrectly labels the issue as related to Admin Center access." Another person said that his whole organization couldn't log in to Office 365 services.
One Twitter poster helpfully pointed to this Microsoft document that describes creating an emergency account in Azure AD, which can be used when MFA isn't working.
More details on this Azure service outage was captured by veteran Microsoft reporter Mary Jo Foley in this ZDNet article.
Organizations with paid Azure AD subscriptions have the ability to claim service-time credits (no cash compensation) for a service outage under the Azure AD service-level agreement. However, they have to be able to demonstrate that they had no alternative means of access, which seems to be true in this case. Also, the credit isn't automatic. It has to be requested.
Azure AD outages have happened before and can have wide consequences. For instance, last year Microsoft explained a broad Azure AD outage as being due to a lightning strike on a Texas datacenter.
About the Author
Kurt Mackie is senior news producer for 1105 Media's Converge360 group.