Report: 'Meltdown' Patch Did More Harm than Good for Windows 7
Patches that were released in January to protect Windows 7 from the Meltdown flaw may have opened an even worse can of worms for the OS, according to one security researcher.
Ulf Frisk, a security researcher who specializes in direct memory access (DMA) attacks, described the problem this week in a blog post called "Total Meltdown?"
The January patch was intended to address the Meltdown flaw in Intel, IBM POWER and ARM-based processors that emerged in January and theoretically allows a rogue process to read all memory on a system.
"[The patch] stopped Meltdown but opened up a vulnerability way worse...It allowed any process to read the complete memory contents at gigabytes per second, oh -- it was possible to write to arbitrary memory as well," wrote Frisk, who is the author of the PCILeech memory access attack toolkit, and who described himself in a DEFCON 24 presentation in 2016 as a penetration tester specializing in online banking security and working in Stockholm, Sweden.
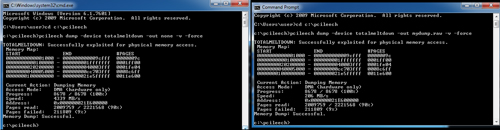 [Click on image for larger view.] Using his PCILeech tool, researcher Ulf Frisk demonstrates the speed of memory dumping from Windows 7 with the January patches at 4GB/s (left). The dump speed is slightly slower when dumping the memory to disk (right). (Image source: Ulf Frisk)
[Click on image for larger view.] Using his PCILeech tool, researcher Ulf Frisk demonstrates the speed of memory dumping from Windows 7 with the January patches at 4GB/s (left). The dump speed is slightly slower when dumping the memory to disk (right). (Image source: Ulf Frisk)
"No fancy exploits were needed. Windows 7 already did the hard work of mapping in the required memory into every running process. Exploitation was just a matter of read and write to already mapped in-process virtual memory. No fancy APIs or syscalls required -- just standard read and write," Frisk said.
The flaw does not affect Windows 10 or Windows 8, according to Frisk.
The problem appears to have been introduced by the Windows 7 patches released in January, during the industrywide scramble to address the Meltdown and related Spectre flaws whose existence was revealed slightly ahead of schedule. Some of the first-generation patches caused reboot and slowdown issues, among other problems.
Frisk said the subsequent March patch for Windows 7 fixed the flaw, and he discovered the problem after the March patch was released.
Posted by Scott Bekker on March 28, 2018