Organizations whose Office 365 environments were set up by third-party partners are at risk of a number of security misconfigurations, a federal computer security watchdog warned on Monday.
In an analysis report titled "Microsoft Office 365 Security Observations," the Cybersecurity and Infrastructure Security Agency (CISA) described four common security misconfigurations found during a multi-month investigation begun last fall. CISA is the new standalone agency within the Department of Homeland Security that functions as the lead national government unit on civilian cybersecurity.
The investigation focused on customers who have used third-party partners to migrate their e-mail services to Office 365. The CISA report did not say how many customer environments it looked at, how large the organizations were in terms of seats or revenues, how widespread the problems were at those sites, or what kinds of third-party partners were involved.
The conclusion, however, was stark. "The organizations that used a third party have had a mix of configurations that lowered their overall security posture (e.g., mailbox auditing disabled, unified audit log disabled, multi-factor authentication disabled on admin accounts)," the report said. "In addition, the majority of these organizations did not have a dedicated IT security team to focus on their security in the cloud. These security oversights have led to user and mailbox compromises and vulnerabilities."
The report details five Office 365 configuration problems, with some of them exposing administrator username/password prompts to attack without multifactor authentication (MFA) protections in place, others involving audit logs being left off, and another allowing attackers who had compromised on-premises accounts to move laterally into the cloud.
The main MFA problem involved organizations that didn't set up MFA for the Azure Active Directory (AD) Global Administrators in an Office 365 environment. Microsoft does not require MFA by default in creating the accounts, and many organizations don't change the setting. The report notes that the Azure AD Global Administrator accounts are the first ones created and are required to configure the tenant and migrate users. "These accounts are exposed to internet access because they are based in the cloud. If not immediately secured, these cloud-based accounts could allow an attacker to maintain persistence as a customer migrates to O365," the report warned.
A related problem flagged by CISA involves legacy protocols that don't support MFA. Those include POP3, IMAP and SMTP. While the report acknowledges that users with older e-mail clients may need these less secure protocols, efforts should be made to limit their use to specific users and to wean the organization off of those protocols as quickly as possible.
Of all the problems highlighted in the report, CISA stressed enabling MFA as a best practice: "This is the best mitigation technique to use to protect against credential theft for O365 users."
Auditing is another commonly discussed problem in Office 365 security circles. Mailbox auditing was disabled by default prior to January 2019, meaning organizations trying to investigate potential breaches often discovered they had no logs to look at if they hadn't enabled the feature. CISA urged organizations whose Office 365 configuration was set up prior to January of this year to ensure that mailbox auditing is enabled.
The analysis report also pointed to another logging feature which is still disabled by default -- the unified audit log. That log records events from several Office 365 services, including Exchange Online, SharePoint Online, OneDrive, Azure AD, Microsoft Teams and Power BI. Administrators can enable the unified audit log in the Security and Compliance Center.
Another configuration choice that can lead to security problems involves password sync using Azure AD Connect, the report states. A useful migration tool designed to create Azure AD identities from on-premises identities or to match previously created Azure AD identities with on-premises AD identities, Azure AD Connect can cause security problems in certain cases.
Posted by Scott Bekker on May 13, 20190 comments
Buried in Microsoft's slew of Build-related announcements this week was an expansion of the co-sell program that has already incented the Microsoft field to sell billions of dollars worth of partners' solutions.
Begun as a program for Azure ISVs, the Microsoft co-sell program was a way for Microsoft to get its own salesforce selling the partners' cloud infrastructure-based solutions. Under co-sell, the Microsoft field got 10 percent of the total value of the ISV partner solution, paid by Microsoft, for landing a sale.
Microsoft said at the Build show in Redmond on Monday that nearly 3,000 ISVs whose solutions run on Azure have generated more than $5 billion in revenue over the past 12 months with the co-sell program. That figure is roughly in line with previous figures the company has released about the scale of the co-sell program.
Now Microsoft is leveraging its massive channel to expand the program in two ways.
First, Microsoft is expanding co-sell beyond Azure. It will now encompass Microsoft 365, Dynamics 365 and Power Platform. In a statement, Microsoft said the idea is "to create deeper collaboration in selling line-of-business applications." The capabilities are planned for availability at the start of Microsoft's fiscal year on July 1. The roadmap also calls for later expansions to Office 365 and Dynamics 365 add-ins.
Next, Microsoft is expanding sales incentives beyond its own salesforce. Now Microsoft channel partners will be able to resell eligible ISV solutions through the Microsoft Cloud Solution Provider (CSP) program. "For all ISVs, small and large, this effectively offers 'channel as a service' to accelerate customer acquisition through one of the world's largest distribution channels," the statement said. It was not immediately clear if the field sales incentives would be changed for fiscal year 2020 or what those incentives would be for resellers representing other ISVs' solutions through Microsoft's engine.
Helping to power the co-selling opportunities is the introduction of what Microsoft describes as "transactable seat-based SaaS capabilities for AppSource and Azure Marketplace."
The automation and incentives in the expanded co-selling program, especially on the partner-to-partner (P2P) side, represent an important new phase of the Microsoft Partner Network (MPN). With the hundreds of thousands of partners in the MPN worldwide, the ability for those partners to connect through the Microsoft marketplaces they already use with (ideally) little friction could rapidly accelerate P2P revenues.
Posted by Scott Bekker on May 07, 20190 comments
VMware infrastructure will run on the Microsoft Azure cloud with full support from both companies under a partnership announced Monday.
CEOs of Microsoft, VMware and VMware majority owner Dell Technologies Inc. announced the deal at Dell Technologies World in Las Vegas.
The arrangement follows a controversial recent effort by Microsoft to conduct its own implementation of a VMware technology integration for Azure in a way that was not supported by VMware. It also comes several years after a similar VMware-Amazon Web Services deal.
Other parts of the expansive partnership include support for managing Office 365 across devices via VMware Workspace ONE, integration by VMware of support for Microsoft's forthcoming Windows Virtual Desktop (WVD), and future work on networking and on delivery of Azure services for VMware on-premises customers.
In a statement, Microsoft CEO Satya Nadella positioned the deal as part of Microsoft's recent pattern of working closely with sometimes bitter, or at least partial, competitors to advance common customer interests. "At Microsoft, we're focused on empowering customers in their digital transformation journey, through partnerships that enable them to take advantage of the Microsoft Cloud, using the technologies they already have," Nadella said.
Scott Guthrie, executive vice president for Microsoft's Cloud and Enterprise Group, expanded on the theme in a blog post, putting the VMware deal in a line of agreements that includes SAP, Red Hat, Adobe and Citrix.
Called Azure VMware Solutions, the main element of the deal is technology built on VMware Cloud Foundation to run VMware workloads natively on Azure. "Customers can now seamlessly run, manage and secure applications across VMware environments and Microsoft Azure with a common operating framework," Guthrie wrote in his blog post. "Customers will be able to capitalize on their existing VMware investments, skills and tools, including VMware vSphere, vSAN, NSX and vCenter while leveraging the scale, performance and innovation of Azure."
In addition to giving customers the ability to manage on-premises and Azure clouds from within their current set of VMware tools, the two companies position the integration as a strong solution for application migration and modernization, datacenter resizings and disaster recovery/business continuity.
Azure VMware Solutions is available immediately in two Azure regions -- U.S. East and U.S. West -- with availability in the West Europe region coming shortly, according to a Microsoft FAQ. While it is sold by Microsoft, backed by the Azure service-level agreement and supported by Microsoft and VMware, it was developed in collaboration with VMware-certified partner CloudSimple. Additionally, a second version is being developed for release later this year by Virtustream, a Dell subsidiary.
The other immediate piece of the partnership will allow VMware Workspace ONE customers to manage Office 365 on devices using VMware's toolset. On stage Monday, VMware CEO Pat Gelsinger described the arrangement as ending a dilemma for customers. "We've solved this battle that we've been having -- is it going to be a Workspace ONE device or a Microsoft Intune device? Gone," Gelsinger said. He said Workspace ONE would have best-in-class support for Office 365, Microsoft 365, Windows 10 and Azure Active Directory.
Also getting "first-class citizen" status within VMware infrastructure will be WVD, Gelsinger said. WVD is currently a Microsoft public preview for a service that delivers a multisession Windows 10 experience, optimizations for Office 365 ProPlus and support for Windows Server Remote Desktop Services (RDS) desktops and apps. VMware will extend the capabilities of WVD through VMware Horizon Cloud on Microsoft Azure. A tech preview is expected by the end of this calendar year.
Longer-term, the companies are exploring integrations between VMware NSX with Azure Networking and exploring bringing specific Azure services to VMware on-premises customers. No specific timeframe was immediately available for those efforts.
Posted by Scott Bekker on April 29, 20190 comments
Microsoft, which has been approaching a $1 trillion market capitalization for about a year, crossed the big business milestone in after-hours trading on Wednesday after outperforming Wall Street expectations with its third quarter earnings.
Microsoft was in a tight race among big tech companies last year with Apple, Amazon and Alphabet to reach the $1 trillion threshold. Apple made it first with Amazon following later, although both fell back below $1 trillion later in the year.
The milestone comes after Microsoft's stock had climbed 34% over the past year and then spiked another 3% after the earnings results Wednesday.
Ongoing strength in its cloud business and a recovery on the Windows side helped power a strong third quarter for Microsoft.
In results released after markets closed Wednesday, Microsoft reported earnings of $30.6 billion, an increase of 14% over the year-ago quarter and well ahead of analysts' expectations. Other headline figures included a 25% gain in operating income to $10.3 billion, a 19% gain in net income to $8.8 billion and a 20% increase in diluted earnings per share to $1.14.
CEO Satya Nadella pointed to the customer demand for Microsoft's constantly evolving cloud services as a key factor for the reporting period, Microsoft's third quarter, which ended March 31. The company pegged commercial cloud revenues at $9.6 billion for the quarter. That's a 41% jump year-over-year on an already large figure.
Inside those cloud revenues, Microsoft's strategic Azure cloud computing platform was a key growth driver. Microsoft reported 73% revenue growth for Azure. Office 365 Commercial revenue also continued to plow ahead, with 30% revenue growth. On the consumer side, Office 365 Consumer subscribers increased to 34.2 million.
One other business growth area for cloud was Dynamics 365, Microsoft's cloud platform for its ERP, CRM and other business applications. Dynamics 365 revenues increased 43% compared to the year-ago quarter.
Last quarter, the Intel chip shortage was a problem for Microsoft, with Chief Financial Officer Amy Hood at the time attributing a smaller overall PC market to the timing of chip supply to Microsoft's OEM partners. While in Q2 Windows OEM Pro revenue dropped by 2% and non-Pro revenue fell 11%, no such problems existed in Q3. Microsoft reported Wednesday that Q3 Windows OEM revenues were up 9% year-over-year. Revenues for Microsoft's own Surface products, meanwhile, were up 21% in the quarter.
In other highlights:
- LinkedIn, which Microsoft purchased in 2016 for $26 billion, continued to perform well in the third quarter, with revenue increasing 27%.
- Enterprise Services revenues increased 4%.
- Gaming revenue was up 4%.
- Search revenue increased 12%, excluding traffic acquisition costs.
Posted by Scott Bekker on April 24, 20190 comments
The ongoing security and public relations mess at Wipro, a massive IT outsourcing company based in India with many major U.S. customers, provides an object lesson in how not to handle a security incident as a managed service provider (MSP).
The story was broken this week by Brian Krebs at his respected security blog Krebs on Security. Official information from Wipro has been slow to come out and inconsistent, which is part of the problem.
Krebs approached Wipro earlier this month after hearing about a breach from several sources. According to his latest reporting, a first Wipro employee fell victim to a phishing attack on March 11, with another 22 employees falling for a second round of phishing attacks on March 16 to 19. As of Wednesday, the attack was still ongoing with more than 100 Wipro endpoints "seeded with" a ConnectWise product for remote control of client systems, as Krebs phrased it. Using the compromised Wipro systems as a jumping-off point, attacks have been launched against at least 12 clients, Krebs reported.
One Wipro customer source that Krebs spoke to worked at a large retailer and said the attackers used the access for gift card fraud at the retailer's stores.
Yet Wipro at first stonewalled Krebs' requests for comment, then released a non-informative statement before eventually acknowledging the breach to an Indian newspaper after Krebs published his first blog. Additionally, the company contested Krebs' timeline without providing one of its own, and appears to be passing off the forensic work of its customers as its own.
Krebs summarized Wipro's ham-handed public response this way:
- Ignore reporter's questions for days and then pick nits in his story during a public investor conference call.
- Question the stated timing of breach, but refuse to provide an alternative timeline.
- Downplay the severity of the incident and characterize it as handled, even when they've only just hired an outside forensics firm.
- Say the intruders deployed a "zero-day attack," and then refuse to discuss details of said zero-day.
- Claim the [indicators of compromise] you're sharing with affected clients were discovered by you when they weren't.
The PR and communication lessons are important, but the substantive security component is even bigger. A major aspect of the market value of an MSP is the expectation that the MSP will be the strongest link in a customer's security chain and be more aware of security all along the chain than the customer could be. For an MSP to be the weakest link, and have to be alerted to its own security problems by customers, is pretty tough to recover from.
Posted by Scott Bekker on April 18, 20190 comments
Have you or your clients had any problems with Azure consumption overages?
It turns out that Microsoft is counting on customers to end up paying more for Azure than they may have planned to.
During Microsoft's last earnings call in January, CTO Amy Hood highlighted Azure consumption overages as a source of growth for the company.
"As a reminder, strong performance in larger, long-term Azure contracts, Azure consumption overages, and pay-as-you-go contracts will drive bookings growth and in-period revenue but will have a limited impact on unearned revenue," Hood said during the call.
There wasn't a direct dollar figure attached, and Hood's comment downplays the total a bit. But when you're a $110 billion revenue company, any amount of money that's worth bringing up in a half-hour call with investors qualifies as a significant sum.
We'd like to hear your stories about Azure consumption overages. How did the overage happen in your or your customer's case? How much did it cost? How did you address the problem and have you been able to contain it since? Drop us a note at [email protected].
Posted by Scott Bekker on April 11, 20190 comments
Many organizations are under some risky misconceptions when it comes to the compliance and security of their Office 365 environments.
That's the upshot of a new 37-page report by CollabTalk LLC and the Marriott School of Business at Brigham Young University titled "Organizational Security & Compliance Practices in Office 365." The report, released last week, was commissioned by Spanning Cloud Apps, RecordPoint, tyGraph, Rencore and Microsoft. (RCPmag.com sister site Redmondmag.com is an in-kind sponsor of the research.) It's based on surveys of more than 270 IT professionals, executives and managers across 19 industries, and includes commentary from several Microsoft Most Valuable Professionals (MVPs) and experts.
In short, the report found that those who believe Microsoft is doing a good job with security and compliance may not be taking the baseline steps required to ensure their environments are safe and in compliance -- in other words, they may not be doing the basic things that Microsoft's tools rely on to help ensure protection. And those who don't believe Microsoft protections are enough tended not to be aware of all the steps Microsoft takes on their behalf.
Specifically, the report said that:
- Of those that thought Microsoft security was sufficient, 80% of respondents have either not run security and compliance checks, or do not know if they have.
- Of those who did not think the current security protection offered by Microsoft was sufficient, 57% of respondents were not aware of Microsoft's security division.
- Of those who did not think the current security protection offered by Microsoft was sufficient, 71% of respondents were not aware of Microsoft's overall security and compliance strategy.
One of the MVP commenters, Matthew McDermott, lays responsibility for this gap squarely on the organizations, which are themselves struggling to keep abreast of the many administrative tools, settings and options within Office 365 components and dealing with hybrid environments that involve many more platforms than just Office 365.
"The gap presented in this research is not from a lack of features, vision or direction from Microsoft; the gap comes from within organizations," said McDermott, Spanning's principal technical marketing engineer and the Conference Chair for Office & SharePoint Live!, an event run by RCPmag.com's parent company, in a statement about the report. "Companies must invest in personnel and tools to ensure compliance and secure systems. It's not enough, with today's threat landscape, to be reactive. You need to be proactive in your approach to keeping your assets and customer data safe and secure."
Another of the MVPs, Erica Toelle, product evangelist at RecordPoint, portrayed the gap as a painful step in a journey toward a better overall situation on security and compliance. "Before the cloud, people managed security and compliance all on their own. Outsourcing this to Microsoft is a good idea. Microsoft has more budget to hire the industry-leaders, so they are more secure. People don't perceive this because their understanding is immature. They don't know how much Microsoft is protecting them or not. They also don't really have complete control over the situation," Toelle stated in the report's conclusion.
Recommendations in the report include approaching security and compliance more holistically, identifying feature gaps and creating an operational strategy for addressing them, conducting inventory audits, creating training plans, developing governance and change management programs and committees, and setting up pilot programs to understand the latest features and capabilities of Office 365.
The report is available from the Spanning Web site here.
Posted by Scott Bekker on April 01, 20190 comments
Microsoft on Thursday released previews for two new cloud-based security services in advance of the RSA Conference 2019 next week.
Microsoft Azure Sentinel is a native security information and event management (SIEM) tool that runs in Microsoft's public cloud. Microsoft Threat Experts is a new "managed threat hunting service" within Windows Defender Advanced Threat Protection (ATP).
Ann Johnson, corporate vice president for Cybersecurity Solutions at Microsoft, touted Azure Sentinel as "the first cloud-native SIEM within a major cloud platform" during a media briefing on Wednesday.
Johnson said Sentinel was built from scratch with the help of industry partners as a modern security tool to collect, parse and present security data from users, devices, applications and infrastructure, both on-premises and in the cloud. Like many of Microsoft's current initiatives, key selling points are the flexible and scalable nature of having the solution running in the cloud and the ability to leverage Microsoft's artificial intelligence (AI) infrastructure and expertise.
At the same time, Microsoft also championed the tool's potential to cut both administrative burdens of on-premises SIEM approaches and the time wasted on inconsequential SIEM alerts.
"I don't need to have people maintaining infrastructure, patching, dealing with upgrades, things like that. I've just got my people focused on finding threats," said Eric Doerr, general manager of the Microsoft Security Response Center (MSRC), in a video about the MSRC's dogfooding of Azure Sentinel.
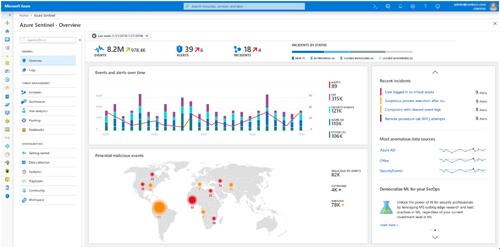 [Click on image for larger view.] The dashboard for the public preview of the Microsoft Azure Sentinel cloud-native SIEM. (Source: Microsoft)
[Click on image for larger view.] The dashboard for the public preview of the Microsoft Azure Sentinel cloud-native SIEM. (Source: Microsoft)
Johnson put the alerts in the context of the IT security skills gap. "The cybersecurity landscape is at a point where the attackers do have an advantage due to a lack of skilled cyberdefenders. With an estimated shortfall of over 3 million security professionals by 2021, there simply are not enough defenders to keep pace with the growing profit opportunity that cybercrime offers," she said. "Existing defenders are overwhelmed by threats and alerts. They often spend their days chasing down false alarms instead of doing what they do best, investigating and solving complex cases."
Microsoft contends that its machine learning (ML) algorithms and knowledge from handling trillions of signals each day inform the Sentinel tool.
Pricing has not been set for Azure Sentinel. The preview is free and licensed Office 365 customers will be able to import data into the tool for free as an ongoing feature once the service is generally available.
The other preview, Threat Experts, is a high-end service for security operations centers. The intent is again to use Microsoft's expertise, AI/ML resources and massive global signals collection to provide context around security alerts that could help organizations find, prioritize and respond to security problems. The service consists of attack notifications that are supposed to be tailored to an organization's needs and the availability of Microsoft experts who can be engaged on demand.
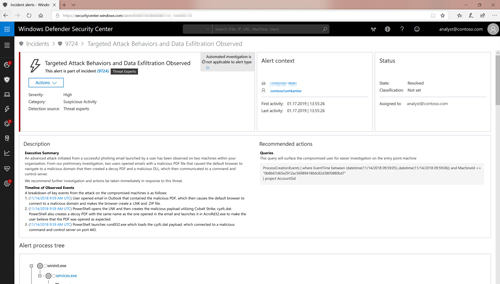 [Click on image for larger view.] Microsoft Threat Experts provides customized alerts in the Windows Defender Security Center. (Source: Microsoft)
[Click on image for larger view.] Microsoft Threat Experts provides customized alerts in the Windows Defender Security Center. (Source: Microsoft)
"Not every organization has access to the level of human expertise they need. Microsoft is now offering our security experts as an extension of our customers teams," Johnson said. "Experts provide the insights our customers need to get additional clarification on alerts, including root cause or scope of an incident, suspicious machine behavior and next steps if faced with an advanced attacker. They can also help determine risk and protection regarding threat actors campaigns or emerging attacker techniques."
Although the new Threat Experts service is also in preview, customers will already need to have Windows Defender ATP to access it. The Windows Defender ATP platform is a toolbox of prevention, detection, investigation and response tools for enterprises. Threat Experts joins elements like attack surface reduction, endpoint detection and response, automated investigation and remediation, Secure Score and advanced hunting tools. Windows Defender ATP is available only in Microsoft's most expensive licensing packages, such as Windows 10 Enterprise E5 and Microsoft 365 E5.
Posted by Scott Bekker on February 28, 20190 comments
A report this week from subscription technology site The Information suggests that Microsoft and VMware are drafting a deal that would make it much easier for enterprise customers to move VMware workloads to the Azure public cloud.
The historical rivals are jointly working on the integration and could be within weeks of an announcement, according to article author Kevin McLaughlin, who attributed the information to "a person with direct knowledge of the project and six others who have been briefed on it."
The arrangement reportedly involves VMware's server virtualization software. Neither Microsoft nor VMware are commenting. If true, it represents another example of Microsoft setting aside long-running competitive fights -- in this case, between VMware hypervisor technology and Microsoft's own Hyper-V offerings -- in favor of attracting increased workloads to the Azure public cloud and positioning Microsoft better for the more strategic fight with its larger public cloud rival, Amazon Web Services (AWS).
VMware already has a similar arrangement with AWS.
"While it is already possible to move computing jobs running on VMware inside private data centers to Azure, it requires extensive technical work. The new software Microsoft and VMware are developing aims to significantly speed up this process, making it cheaper for them to accomplish," the article by Kevin McLaughlin stated.
The deal follows a controversial move by Microsoft in November 2017 to build software on its own to allow VMware computing jobs to run on Azure, a move that VMware challenged at the time.
One interesting personnel detail in the article that supports the idea that the companies are working together is the presence of Ray Blanchard, identified as the former VMware executive in charge of the partnership with AWS. Blanchard joined Microsoft a year ago.
Posted by Scott Bekker on February 27, 20190 comments
One of the most dynamic International Association of Microsoft Channel Partners (IAMCP) chapters in the United States will hold a party this fall to celebrate its tenth anniversary.
The SoCal IAMCP chapter will hold a tenth anniversary party in Irvine, Calif., on Oct. 24, a Thursday. Formed 10 years ago this July with Justin Slagle as its original president, the Southern California chapter had strong engagement and support from Microsoft from the beginning.
As a senior partner development manager at Microsoft, Slagle is helping organize the 10-year celebration with a heavy hitting cast of Microsoft speakers. In fact, the SoCal IAMCP is billing the event as a way for members and guests to get some of the benefits of Microsoft Inspire without the $2,000 price tag of the annual worldwide partner conference in Las Vegas.
Guest speakers will include Microsoft Channel Chief Gavriella Schuster; Brent Combest, a U.S. general manager for Microsoft; Beth Cavanaugh, Microsoft's national partner sales director; SoCal IAMCP's current president, Eddie Bader; and some of the chapter's past presidents, a list that includes Slagle, Ro Kolakowski, David Gersten, Dave Seibert and Eric Klauss.
The event will run most of the day with invite-only sessions from 10 a.m.-2 p.m., keynote sessions from 2 p.m.-5 p.m. and a party from 5 p.m.-8 p.m.
Tickets start at $249, and registration fees will go toward buying a car to be raffled off at the party. Details are available at https://iamcpparty.com/.
Posted by Scott Bekker on February 19, 20190 comments
This week brought the next logical step in the evolution of the Azure Stack with the unveiling of a ruggedized version from Dell EMC.
From the beginning, Microsoft's vision for the Azure Stack involved situations where you're getting your hands dirty.
The Azure Stack is supposed to bring much of the power of Azure cloud computing out to the edge, where users can run full artificial intelligence (AI) or other processing-intensive workloads without waiting to connect to the cloud.
Use cases cited by Microsoft CEO Satya Nadella in 2018 included early adopter Chevron deploying Azure Stack on oil rigs, for example. A demo video last year featured Scott Montgomery, a senior industry solutions manager at Microsoft, driving around in a one-ton Chevrolet Suburban decorated with the Microsoft logo and loaded with an Azure Stack in the cargo area. The point was to highlight disaster relief scenarios, remote power line inspections with a drone and other scenarios.
Yet the first implementations of Azure Stack, which is sold as a complete hardware and software solution by a handful of OEM partners, were primarily designed for the standard datacenter, which is an exceptionally clean room in most cases. That was a good place to start as many of the less photogenic implementations of Azure Stack call for data processing at a branch office or a remote facility that doesn't require the server kit to be mobile once it's installed.
Later this quarter, Dell EMC will ship a ruggedized version dubbed the Dell EMC Tactical Microsoft Azure Stack.
 The back side of the Dell EMC Tactical Microsoft Azure Stack. (Source: Dell EMC)
The back side of the Dell EMC Tactical Microsoft Azure Stack. (Source: Dell EMC)
"Tactical Azure Stack is the first and only ruggedized Azure Stack product available for tactical edge deployments," wrote Paul Galjan, senior director of Microsoft Hybrid Cloud at Dell EMC, in a blog post announcing the system.
The Azure Stack is a two-person lift at 380 pounds. That weight is light enough to qualify the system as fully mobile or highly portable given that it can be moved by two people. It's also a reasonable weight considering the 41.5" high and 25.6" deep box includes all the servers, storage and networking gear needed to run the Azure software. There's an option to use additional "core" transit cases to go up to the full node limits of Azure Stack.
"The Tactical Microsoft Azure Stack unlocks a wide variety of use cases for government, military, energy and mining applications," Galjan said. "It can also be ideal in forward deployments and mobile environments in marine, aerospace and other conditions that require MIL-STD 810G compliance."
Also this week, Microsoft, which integrated the Azure Stack with the Azure Government cloud last year, unveiled new Azure Data Box products for Azure Government. The on-premises appliances include the Azure Data Box Edge, available now in preview; the Azure Data Box Gateway and Azure Data Box, both available in March; and the Azure Data Box Heavy, set for availability in the middle of the year.
Posted by Scott Bekker on February 06, 20190 comments
Microsoft is connecting its most significant-breadth partner business model with a strategic technology initiative in a way that could unlock truly scalable partner-to-partner (P2P) business interaction within its giant partner ecosystem for the first time.
"Today, we're excited to announce that by connecting our marketplace to our cloud solution provider companies, through our channel, we're enabling ISVs that publish their solutions to our marketplace to have unfettered access to our entire ecosystem directly," said Gavriella Schuster, corporate vice president of Microsoft One Commercial Partner (OCP), during a media briefing on Tuesday.
Cloud solution provider, or CSP, is Microsoft's most important broad-based partnering program. Under the program, partners sell mostly Office 365, but also other Software as a Service (SaaS), Azure cloud and other products as part of their own service bundles, giving them better control over margins and the ability to put their own vertical or specialized service wrappers around Microsoft offerings.
The marketplaces involved in the announcement are AppSource and the Azure Marketplace, two Microsoft marketplaces that currently include more than 8,000 solutions from more than 4,000 ISVs and other partners.
In the past, CSPs could search through AppSource or the Azure Marketplace for complementary solutions, but the process was manual and then would require reaching out to an ISV to figure out how to enter a reselling relationship.
When the feature that Schuster announced is implemented in March, an ISV entering an application into AppSource or the Azure Marketplace will, with one click, be able to enable all CSPs in the Microsoft ecosystem to resell the product, according to Microsoft. The marketplaces also allow repeatable service packages from solution providers, not just applications by ISVs. Those solutions will also work with the new P2P system.
"One click will give a partner's solution exposure through tens of thousands of Microsoft cloud partner resellers and about 17 million partner sellers who work for them. Plus, their solution will be searchable by more than 75 million customers and thousands of Microsoft sellers," Schuster said. "By transacting through our Cloud Solution Provider channel, partners will be able to take their managed service offerings and package them with other first- and third-party solutions in the marketplace to create specialized offerings for their customer."
The ability for partners to open their solutions to CSPs is only one element of the near-term changes coming to the marketplace. Other elements include simplifying the experience, improving the search experience for both partners and users so that natural-language queries are more likely to return relevant results, and a private marketplace option for enterprises. Schuster said those enterprise-ready private marketplaces will also make it possible for partners to customize terms for any specific customer.
Additionally, Microsoft will be engaging in a parallel push to develop the Dynamics 365 and Power platform ISV ecosystems. "We recognize that technology is only part of what makes ISVs successful, it is important that the business side is equally as robust," said Steven Guggenheimer, corporate vice president for ISV & AI engagement at Microsoft, in a blog post Tuesday. "Being able to publish once to merchandize across storefronts to all Microsoft's customers, sellers and partners will open new growth opportunities to most ISVs."
In an interview Tuesday, Schuster said Microsoft has been working for the last 18 months to create a core commerce back-end that will support multiple storefronts, such as Azure Marketplace and AppSource.
"What the single store does is it enables our partners to have the one place they come in, get their applications certified, get it into the marketplace, and then we will promote it through multiple storefronts, whether that's our own or even syndicated through other partnerships that we have. It's about helping our partners with solutions and services get their solutions more discoverable," she said.
Schuster said the P2P work builds on what Microsoft started internally with the OCP Catalog, which was an initiative for Microsoft's internal field sellers to find relevant partner solutions that they could take to customers. "We refined how do you search and how do you label and how do you put metadata across those solutions, and then that's what we're using as our best practice into the marketplace," she said.
The other real value, after broad market exposure, comes in automating the process of provisioning and invoicing for ISVs and other solution partners.
Schuster, who has been talking about creating back-end engines for P2P connections at a strategic level for several years, calls the marketplace-to-CSP connection a game-changer. "This is a massive investment for the company that underpins our whole partner strategy," she said.
Microsoft has over-promised before on marketplace initiatives, but this move represents a different type of effort. It creates a back-end infrastructure to support P2P connections on top of a Microsoft infrastructure. If the implementation is strong (a big "if" at this stage), Microsoft wins when its services sell as part of a bundle; ISVs win as their solutions get wider attention from other partners, customers and Microsoft sellers; and CSPs win by being able to expand their service packages with much less friction.
Posted by Scott Bekker on February 05, 20190 comments