The industrywide push in recent years toward encrypting Web traffic isn't just for good guys.
Encryption has always been neutral, as useful to bad actors for hiding nefarious activity as it is for legitimate users trying to protect their data from those trying to steal it.
New research from SophosLabs documents how widespread the use of HTTPS connections is becoming in malware circles, especially for communicating back to command-and-control servers (C2).
SophosLabs on Tuesday reported on a representative sampling of malware analyses the research team has conducted over the past six months.
"Out of all the malware that made some kind of network connection during their infection process, about 23% communicated over HTTPS, either to send or receive data from the C2, or during installation when they may use HTTPS to conceal the fact that they are retrieving malicious payloads or components," SophosLabs threat researcher Luca Nagy wrote in the blog post describing the research.
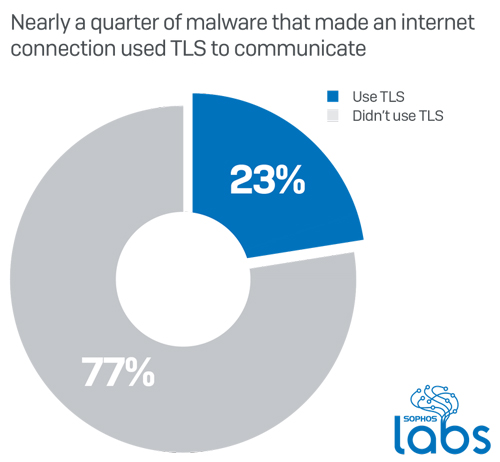
Not all types of malware communicate equally over TLS. Information-stealing trojans made up only 16 percent of the samples SophosLabs tested during the six-month period, but of those, 44 percent used TLS over standard HTTPS ports. Ransomware, which does its damage in other ways, was less likely to use encryption when calling home.
Sophos released the research Tuesday in conjunction with the launch of a new firewall, which features more advanced SSL inspection, including support for TLS 1.3 without requiring downgrading, new policy tools and performance improvements. More detail on XG Firewall v18 is available here.
Posted by Scott Bekker on February 18, 20200 comments
As Microsoft herds its collaboration users toward the Teams platform, Teams voice services have grown rapidly, as well. Even with the rapid gains, usage of voice services in Teams represents a tiny fraction of overall Teams adoption. That lag reflects the challenges unique to voice, from network optimization to working with carriers to requirements for provisioning users.
One early technology partner of Microsoft's on Teams voice is trying to spur voice adoption with a new partner program. NuWave Communications on Thursday launched a white-label program to help partners and resellers get customers into voice plans without the need to build up expertise on daunting voice technologies.
Las Vegas-based NuWave now offers the white-labeling of iPilot, which is the company's relatively new provisioning portal for Teams Direct Routing customers. The iPilot portal works with NuWave's Direct Routing calling plans.
Mark Bunnell, chief operating officer for NuWave, contends that the time is right for voice services through Microsoft. "When Office 365 is the center of your universe as a business, it's really easy to think about getting Teams voice and bringing it all together," Bunnell told me in an interview Thursday.
 "Teams right now is equated to the gold rush. Like the gold rush, nobody brought clothes or food so they froze to death on the way up there."
"Teams right now is equated to the gold rush. Like the gold rush, nobody brought clothes or food so they froze to death on the way up there."
Mark Bunnell, COO, NuWave
As they have with Lync, Skype and other Microsoft services, however, partners struggle with the leap from IT infrastructure to voice services.
"Teams right now is equated to the gold rush. Everyone is trying to get a piece, everyone is trying to turn on a Teams practice. Like the gold rush, nobody brought clothes or food so they froze to death on the way up there," Bunnell said of the rough experiences some customers and partners have had with voice services.
NuWave's approach stems from the company's 20-plus year history in SIP Trunking, hosted PBX, unified communication as a service (UCaaS) and related fields. "We've taken the extremely complex and we've made a turnkey solution that doesn't make [the partners] be technical," Bunnell said.
First, iPilot leverages NuWave's experience from several years of Teams voice deployments, covering migrations from Microsoft's older voice platforms or other sources and handling the PowerShell elements of provisioning users within a customer's Microsoft tenant. As the provider of the lines, the company also saves time in setting up proofs-of-concept from a process that can take several weeks in many cases to under an hour, Bunnell said.
After the set up, NuWave provides end-user training materials, such as user guides and videos, to get customers up to speed quickly. With the white-label program, partners have the ability to customize the pricing customers see and the phones they want to offer, he said.
"It really enables you to turn up a customer, get them fully trained and move on to the next one," Bunnell said.
Voice services aren't for every Office 365 partner. But for those looking for a way to spin up a quick, low-investment Teams voice practice, NuWave is saying the right things.
Posted by Scott Bekker on February 13, 20200 comments
One of the most engaging voices in the IT channel security community, Ian Thornton-Trump, is on the move. RCP caught up with Thornton-Trump last month just as he was getting started in a new role at Cyjax, an 8-year-old U.K.-based cyber threat intelligence provider.
Thornton-Trump joins Cyjax as chief information security officer. The dual role includes internal cybersecurity responsibilities along with helping the company prepare for an expansion into the U.S. channel. At the same time, Thornton-Trump is piloting a cyber threat intelligence workshop for CompTIA.
We talked to Thornton-Trump about why he thinks the moment is right for managed service providers (MSPs) to get involved in security threat intelligence. Edited excerpts of the conversation are below.
Two major security issues a few years ago got Thornton-Trump thinking seriously about security intelligence and the channel.
"I go back to really WannaCry and EternalBlue. The US-CERT and Microsoft made noises prior to that malware being weaponized. At that time it was about 58 days before the first impactful attacks happened from when Microsoft announced that there is a vulnerability in [its Server Message Block protocol], and they were pushing patches even for out-of-date operating systems. Now, the threat intelligence analysis of that is kind of, 'Holy crap, if Microsoft is going to support unsupported operating systems and issue and out-of-band patch for it, it must be super bad.'
"For whatever reason, I don't think people were paying attention. When you look at some of the big dogs out there, Maersk and Merck, the pharmaceutical company, that then got hit by NotPetya, which leveraged the same attack, essentially, as WannaCry, you kind of wonder if anybody was listening out there.
"So I felt like for the small/medium business practitioners and those MSPs that service them, no one was really providing good, credible intel to small and medium-sized business [SMB] customers about this stuff."
 "Historically, cybersecurity practitioners and IT practitioners may be somewhat challenged in terms of business communication."
"Historically, cybersecurity practitioners and IT practitioners may be somewhat challenged in terms of business communication."
Ian Thornton-Trump, CISO, Cyjax
In the nearly three years since those attacks, Thornton-Trump believes government agencies in the United States and the United Kingdom have greatly improved their alerting and threat communications. Yet he also contends that MSPs and SMB IT pros need much more help.
"The importance of a government tool to tell you that you're vulnerable means rather than it being the security guy who's all concerned going to the business, it's literally the government telling you that you need to patch."
Thornton-Trump said he sees an opportunity for Cyjax, which offers threat intelligence and associated dashboards, to provide some of the data that will help MSPs make the business case for action.
"Historically, cybersecurity practitioners and IT practitioners may be somewhat challenged in terms of business communication. Having data from a third-party trusted source that says, 'Listen, we have X number of assets that are vulnerable to BlueKeep. We need to disrupt the business operations for a couple of hours to patch and update our infrastructure so that we're not victimized by a cybercrime attack, which in 90 percent of the cases for business today would be a very disruptive ransomware attack requiring weeks and unanticipated financial expenses.'
"We can we can go into boardrooms with our hair on fire. But if when we're challenged by the business to provide a true statement or understanding of the risk, a lot of it falls down because what the practitioners are not doing is coming armed to the fight with the return on investment or the stark warnings from government bodies, law enforcement bodies. I want to close that gap in the channel."
As Cyjax works on a channel program to adapt its cyber threat intelligence offerings to MSP technical and business requirements, Thornton-Trump says the sector has the potential to be a high-value, low-cost revenue opportunity for MSPs and IT service pros.
"I'm excited about the opportunity to take my original message of layered security and now turn it into a true proactive threat model -- modeling and risk management by using intelligence."
At the same time, Thornton-Trump is demonstrating a workshop/course on "Cyber Threat Intelligence" at the CompTIA conference in Manchester, England next month.
"The course is designed to help an MSP or an SMB build its own threat intelligence program using publicly available tools. My idea here is to equip businesses to get in front of cyber attacks, get meaningful data and make appropriate business decisions based on their threat model and their risk profile. I'm really passionate about that. I want to create more capacity."
Both efforts, building a channel program for Cyjax and developing the independent training, are coming at a key time for MSPs, in Thornton-Trump's estimation.
"This is coming at a moment where MSPs are waking up and finding many of their customers victimized by ransomware, which is potentially putting their livelihood at risk. I'm talking about the Cloud Hopper series of attacks, which has now been adapted by cybercriminals who are specifically targeting MSPs and IT service pros. So I think the time is right to get the upper hand and to get the opportunity to get in front of these attacks, and protect customers and ultimately protect the livelihood of businesses."
Posted by Scott Bekker on February 11, 20200 comments
Want to get your Microsoft partner company noticed in 2020? Submit your entry to be included in Redmond Channel Partner's RCP 350 list.
As in previous years, it's a qualitative list of the Microsoft solution provider companies that demonstrate a laser focus on Microsoft technology and a strong commitment to providing great value for their customers.
There are a few requirements -- companies that get listed must belong to the Microsoft Partner Network (MPN), must have major end-user service operations in the United States and should have at least one Microsoft gold competency.
Beyond that, the list is subjective. We're not just looking for the biggest companies or the broadest coverage of Microsoft technologies. Some winners are niche providers, focused on a sliver of the Microsoft stack. Others have a great local reputation. Still others are regular Microsoft regional award winners.
There are a few exciting differences in the list this year. For one, we're expanding from the previous 200 entries to 350. It will still be an elite few of the tens of thousands of Microsoft partners in the United States, but the list will be more comprehensive.
What is more important is where the list will appear. In its final form, the RCP 350 will be posted as a PDF on RCP's sister site, Redmond. Redmond is the premier site where C-level executives, IT decision makers and IT professionals go for their Microsoft infrastructure news and commentary. By appearing in the list on Redmond, your company will be in front of more potential customers interested in the types of expertise you have.
Selection for the list is a judgment made by our editors as a service to readers of RCP and Redmond. There is no cost for submissions or inclusion in the list. Results will be released in July 2020.
The survey is short. There are only 11 questions, including company basics and contact information. Revenues and employee headcount questions are optional. We recommend that you put your main effort into this question: "Briefly explain why the company belongs in the RCP 350." There is effectively no character limit for your answer, although we respectfully request that you keep it to fewer than 500 words for purposes of our sanity here at RCP.
Does your company have what it takes? Fill out the application here by April 3 to make sure you're considered.
Posted by Scott Bekker on February 04, 20200 comments
Surprisingly strong demand for Windows, partly driven by important end-of-support deadlines, was among the major factors helping Microsoft exceed Wall Street expectations for its most recent quarter.
Microsoft on Wednesday evening reported revenues of $36.9 billion and diluted earnings per share of $1.51, both well ahead of consensus analyst expectations. The earnings period covered Microsoft's second financial quarter, which spans the last three months of 2019. The usual growth sources, like Azure, Office 365, Dynamics and LinkedIn, all delivered in the quarter. But Windows, which has been more of a drag of late, was a standout in Q2.
It was the last full quarter before end-of-support deadlines hit on Jan. 14 for Windows 7, Windows Server 2008/R2 and Hyper-V Server 2008/R2.
Microsoft's overall business unit that includes Windows clients is More Personal Computing, and the sector outpaced the company's previous guidance. "Revenue was $13.2 billion, increasing 2% and 3% in constant currency, ahead of expectations as better-than-expected performance across our Windows businesses more than offset lower than expected search and Surface revenue," Microsoft CFO Amy Hood said during the earnings call with investors Wednesday.
The end-of-support effects were strong in the OEM Pro sector, which Hood said makes up roughly 40% of total Windows revenue. Those revenues, she said, "grew 26%, driven by continued momentum in advance of Windows 7 end of support and strong Windows 10 demand."
Windows Server 2008 end-of-support also contributed to overperformance in a different business unit, Intelligent Cloud. "Our on-premises server business grew 10% and 12% in constant currency with roughly four points of benefit from the end of support for Windows Server 2008," Hood said.
End of support was only one among several factors affecting the gains for Windows. On the PC side, market growth was stronger than Microsoft anticipated. It also benefited from comparisons to last year, when a chip shortage was inhibiting OEM partners' ability to ship PCs. Microsoft's More Personal Computing unit also benefitted from revenue growth in commercial products and cloud services, which includes Microsoft 365.
On the server side, Hood also credited some of the growth to Azure Hybrid Benefits, which allow Software Assurance customers to put Windows Server licenses into virtual machines on Azure at a reduced cost.
For the current financial quarter, Microsoft expects the support deadlines that just passed to provide a continuing boost to revenues.
"In Windows, overall, OEM revenue growth should be in the low to mid-single digits and continue to reflect healthy Windows 10 demand, end of support for Windows 7 and the supply chain's ability to meet demand," Hood said. "Growth in our on-premises server business should be high single digits, again driven by strong hybrid demand, as well as some continued benefit related to the end of support for Windows Server 2008."
One variable for Windows revenues in Q3 is a question mark for everyone -- the coronavirus outbreak, which has led to the quarantining of 16 cities in China and prompted Russia to begin closing its border with China.
Hood cited the "uncertainty related to the public health situation in China" as the reason Microsoft's guidance for next quarter in More Personal Computing covers a wider range of revenues than usual.
Posted by Scott Bekker on January 30, 20200 comments
Microsoft CEO Satya Nadella reaffirmed the company's central focus on developers in no uncertain terms this week.
Speaking to financial analysts on Wednesday during a wide-ranging investor call about Microsoft's second quarter earnings, Nadella said, "We want to build the best tool chain."
Then, he got into why:
The statement came in response to a question from Morgan Stanley equity analyst Keith Weiss about Nadella's views on Microsoft's progress with developers since the major GitHub acquisition in 2018.
"We're very excited about what's happening with the developer offering," Nadella said. "I think of what we are doing between Visual Studio and Azure DevOps and GitHub as effectively coming together as a compelling developer's SaaS solution in the same class as any other SaaS solution from Microsoft around productivity and communication."
Most of the talk out of Microsoft lately emphasizes Azure, cloud more generally or artificial intelligence. Nadella's comment to analysts, however, shows that he hasn't forgotten who must make the software giant's offerings work at an individual company level.
In fact, Nadella likes to point out that there are more software engineers/developers in the non-tech sector now than there are in the tech sector itself.
And while Weiss couched his question in the context of whether the developer tools give Azure a competitive advantage over Amazon Web Services and Google Cloud Platform, Nadella steered it back to Microsoft being focused on the needs of developers rather than a need to advance Microsoft platforms.
"We're not focused only on Azure. For developers who use our tool chain, they can target any cloud, any edge device. And so this is not a sort of means to some end; we've always been clear about it, it's an end to itself," Nadella said. "We want to stay true to that ethos of open source, GitHub, and do the best tools."
Now, before things sound too pie-in-the-sky, Nadella reassured the audience of investors that those developer tools as a SaaS business are high-margin for Microsoft and suggested that the tools are optimized for developers coding for the Microsoft ecosystem.
Nadella's profession of love for building tools for developers doesn't have the wild, enthusiastic energy of former CEO Steve Ballmer sweatily pointing and yelling "Developers! Developers! Developers! Developers!"
Yet Microsoft's third CEO's quiet, confident and understated delivery communicates an equally forceful commitment.
Posted by Scott Bekker on January 30, 20200 comments
The U.S. National Security Agency discovered, reported and was publicly credited by Microsoft for a significant vulnerability that is included in the first Patch Tuesday release of the year.
The NSA's public cooperation with Microsoft in defending users of the operating system marks a change from the agency's well-documented past practice of quietly collecting and weaponizing serious OS flaws that are discovered by its researchers.
Microsoft and the NSA offered differing characterizations of the flaw in Windows 10, Windows Server 2016 and Windows Server 2019. While Microsoft encouraged all users to rapidly apply the patch, the structure of Microsoft's extensive vulnerability rating system slightly underplays the severity of the flaw. The NSA, on the other hand, warned that the consequences of not patching would be "severe and widespread."
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) also released an Emergency Directive and Activity Alert regarding the flaw on Tuesday. While CISA's directive only applies to certain federal agencies, the agency's warnings are often heeded by state and local governments and private sector organizations.
In a Cybersecurity Advisory released at the same time as Microsoft's patches, the NSA said:
NSA has discovered a critical vulnerability (CVE-2020-0601) affecting Microsoft Windows cryptographic functionality. The certificate validation vulnerability allows an attacker to undermine how Windows verifies cryptographic trust and can enable remote code execution. The vulnerability affects Windows 10 and Windows Server 2016/2019 as well as applications that rely on Windows for trust functionality. Exploitation of the vulnerability allows attackers to defeat trusted network connections and deliver executable code while appearing as legitimately trusted entities.
Offering examples of ways that validations of trust may be impacted, the NSA cited HTTPS connections, signed files and e-mails, and signed executable code launched as user-mode processes.
"The vulnerability places Windows endpoints at risk to a broad range of exploitation vectors," the NSA statement said in explaining the agency's alarm over the issue. "NSA assesses the vulnerability to be severe and that sophisticated cyber actors will understand the underlying flaw very quickly and, if exploited, would render the previously mentioned platforms as fundamentally vulnerable. The consequences of not patching the vulnerability are severe and widespread. Remote exploitation tools will likely be made quickly and widely available. Rapid adoption of the patch is the only known mitigation at this time and should be the primary focus for all network owners."
On Microsoft's severity scale, however, the vulnerability was rated as being "important" rather than Microsoft's top level of "critical." Microsoft noted that the flaw had not been publicly disclosed, and there were no known public exploits of the flaw currently. Microsoft did give the flaw its "exploitation more likely" rating for both its latest software releases and older software releases. That is the highest level on Microsoft's exploitability index assessment short of flaws for which exploits already exist. Microsoft applies that rating in cases where Microsoft believes exploit code could be created to consistently exploit the vulnerability and when there are past cases where the specific type of vulnerability has been exploited.
Microsoft's technical description of the vulnerability acknowledges the NSA, which is a first. In a separate public statement about CVE-2020-0601, Mechele Gruhn, principal security program manager for the Microsoft Security Research Center, does not name the NSA but does talk about cooperation with security researchers to work on patching newly discovered vulnerabilities.
"This vulnerability is one example of our partnership with the security research community where a vulnerability was privately disclosed and an update released to ensure customers were not put at risk," Gruhn wrote.
Rumblings that a major patch was on the way emerged earlier in the week. The Krebs on Security blog posted an article on Monday with details of the patch collected from sources, and referenced Twitter posts from security industry insiders who indicated something substantial was afoot.
The agency's cooperation reflects a larger debate about the appropriate role of America's digital spy agency. Historically, the organization is known for its offensive capabilities, hiring top researchers to find and exploit vulnerabilities, build them into sophisticated toolsets, and keep those tools secret and productive for as many years as possible. But the recent security/intelligence/public relations disasters involving the EternalBlue tools released by the Shadow Brokers group highlighted a huge self-defeating flaw in the approach. Namely that with the United States being one of the most digitized and Internet-connected countries in the world, when those U.S.-developed tools get into the hands of adversaries of the United States and U.S. businesses, they can do more damage to the U.S. than they could do to their intended targets.
In a statement reported by The Washington Post, a senior NSA official acknowledged the shift in gears represented by the public cooperation on protecting infrastructure versus secretly attacking it.
"This is...a change in approach...by NSA of working to share, working to lean forward, and then working to really share the data as part of building trust," the Post quoted Anne Neuberger, director of the NSA's Cybersecurity Directorate, as saying Tuesday. Krebs on Security's Brian Krebs, apparently reporting from the same NSA news conference, added via Twitter that Neuberger also said this wasn't the first time NSA has reported a vulnerability to Microsoft, but it is the first time it has accepted credit or attribution when Microsoft asked.
The NSA dubs the operation "Turn a New Leaf," and it received praise from security researchers. That said, the agency's strategic mission of exploiting enemy networks undoubtedly remains unchanged.
Yes, the NSA has just helped Microsoft and its more attentive customers patch a flaw. At the same time, is it tinfoil hat territory to bet that other teams at NSA are involved in the race to develop exploits based on the same vulnerabilities, or perhaps have already done so given the agency's head start?
What we have here is a complicated dance. The NSA is playing a slightly more transparent -- and from the standpoint of software vendors and their customers, a more constructive -- role in network security than it has in the past. At least it is playing that role in this specific case. We'll take what we can get.
Posted by Scott Bekker on January 14, 20200 comments
The U.S. agency in charge of cybersecurity is urging organizations in the United States to prepare for potential attacks from Iran in response to the American drone killing of General Qassim Suleimani.
The Cybersecurity and Infrastructure Security Agency (CISA) issued its warning, "Potential for Iranian Cyber Response to U.S. Military Strike in Baghdad," on Monday afternoon. CISA is a federal agency created in 2018 to coordinate with other government entities and the private sector on cybersecurity and critical infrastructure protection.
The drone attack as Suleimani was visiting Baghdad last week is widely expected to prompt counterattacks of some sort from Iran, with Iranian leaders vowing as much in recent days. One of the most rapid ways that Iran can respond is through attacks on computer systems of U.S. businesses and government agencies.
"Iran has a history of leveraging asymmetric tactics to pursue national interests beyond its conventional capabilities," the CISA alert said. "More recently, its use of offensive cyber operations is an extension of that doctrine. Iran has exercised its increasingly sophisticated capabilities to suppress both social and political perspectives deemed dangerous to Iran and to harm regional and international opponents."
A site defacement already occurred over the weekend, when the Web site for the U.S. Federal Depository Library Program was replaced with an image of a bloodied President Trump being punched in the face. Text in English across the bottom of the page read, "Hacked by Iran Cyber Security Group HackerS ... ;)". A CISA spokesperson told the Washington Post that the attacker used a misconfiguration within the content management system to effect the defacement, and that CISA was unable to provide confirmation that the attack had any actual link to Iran.
In a primer section of its alert, CISA recommended that organizations "adopt a state of heightened awareness," "increase organizational vigilance," "confirm reporting processes" and "exercise organizational incident response plans." The document also details mitigation and detection recommendations for advanced persistent threat techniques that Iranian state-sponsored actors are believed to have used in the past, such as spearphishing, credential dumping and attacks involving PowerShell or scripting.
The full alert is available here.
Posted by Scott Bekker on January 06, 20200 comments
This year was as eventful for Microsoft partners as any in this decade.
As the year draws to a close, here's a look at some of the biggest stories that happened in 2019.
1. Ransomware Roared Back
At the beginning of this year, it looked like ransomware might have plateaued. Not so. One of the most damaging computer malware incidents to date happened to Baltimore, when a ransomware attack in May took much of the city's infrastructure offline for weeks and other systems down for month. Meanwhile, a trio of attacks on municipal governments in Florida brought record-setting ransom payouts.
The upshot of all this activity is that managed service providers (MSPs) and other types of Microsoft partners spent a lot of time in 2019 educating customers about ransomware, protecting them from attacks and helping them recover from incidents.
2. Microsoft Opens up 'Channel as a Service'
Microsoft launched a significant effort in calendar 2019 to connect its independent software vendor (ISV) partners with its cloud solution provider (CSP) partners through its marketplaces and incentive structures. The results aren't in yet, but the moves have the potential to take the promise of Microsoft's 300,000-partner-strong channel and convert it into more revenues for everyone involved.
One part involves expanding the multibillion-dollar co-sell program beyond Azure to also include Microsoft 365, Dynamics 365 and Power Platform. The other part involves allowing partners to resell ISV solutions through Microsoft's CSP program.
3. Scuttled IUR/Competency Changes
Microsoft faced a full-scale partner mutiny around the time of its annual partner conference, Microsoft Inspire, in July. A plan disclosed shortly before the Las Vegas conference would have had Microsoft revoking partners' ability to use internal use rights (IURs) to run their businesses.
But a substantial partner backlash, which included a very public Change.org petition, against the planned IUR revocation and some changes to competencies caused Microsoft to reverse course. In the end, Microsoft apologized for the incident and promised to do a better job consulting with partners earlier in the decision process for program changes that would have a major effect on the way partners do business.
4. Azure Lighthouse
Microsoft took a major step to make Azure a friendlier platform for MSPs in 2019. The effort takes the form of a native toolset called Azure Lighthouse.
Using Azure Lighthouse, partners can manage multiple customers in a secure, multitenant environment with automation. Another way to look at it is as a single control plane for service providers to view and manage Azure across their customers. Azure Lighthouse reached general availability in July.
5. Microsoft Hits $1 Trillion
In the race for a $1 trillion market cap, Microsoft seemed like a dark horse, behind Apple, Amazon and Alphabet. Although Apple and Amazon reached the milestone first, Microsoft cleared that hurdle and impressively remained there more consistently than the others. After years of getting kicked around by Wall Street, Microsoft took its place in 2019 as one of investors' most respected companies.
For the Microsoft channel, the market cap provided some positive buzz around the Microsoft brand for much of the year.
As for what to expect in 2020, several big trends are already clear. Azure migration momentum should continue after being spurred by the Windows Server 2008 support deadline next month. The controversy over Microsoft's winning the Department of Defense JEDI contract, and Amazon's contesting of the decision, will continue to roil as the Amazon Web Services (AWS) lawsuit works its way through the courts. And Microsoft will continue to tinker with its partner program levers to urge partners to help make artificial intelligence an everyday technology for customers.
What else will be big next year? We'll find out as it happens.
Posted by Scott Bekker on December 31, 20190 comments
Microsoft set an official date for shutting down Wunderlist -- May 6, 2020.
The announcement presumably brings to a close the drama surrounding the task list app and service, which Microsoft acquired in 2015.
Christian Reber, who as CEO of 6Wunderkinder sold the app to Microsoft, created a stir in September when he Tweeted at Microsoft CEO Satya Nadella and another Microsoft executive about his interest in buying back Wunderlist.
An ax has been hanging over Wunderlist since Microsoft released a preview of the Microsoft To-Do Office 365 application in April 2017. At the time Microsoft said the eventual plan was to retire Wunderlist.
According to a FAQ accompanying the announcement blog on Monday, Wunderlist is not currently accepting new user registrations. After May 6, users will no longer be able to update or edit their lists or tasks. Microsoft provided links in the FAQ to resources for exporting the account or importing lists into Microsoft To Do.
As for why it will discontinue Wunderlist three years after the initial announcement and five years after the acquisition, Microsoft's blog stated that the app is becoming more difficult to maintain as it ages, and that the company is confident that the recent updates to Microsoft To Do make the app a worthy replacement for Wunderlist.
Posted by Scott Bekker on December 10, 20190 comments
The other shoe has officially dropped in the JEDI cloud contract dispute.
After signaling last month that it would challenge the U.S. Department of Defense's process for awarding the massive contract to Microsoft, Amazon formally filed suit on Monday.
The company filed its protest complaint in the U.S. Court of Federal Claims over the Joint Enterprise Defense Infrastructure contract, which is known as JEDI and which could be worth up to $10 billion over 10 years to supply cloud computing services to the DoD.
Public versions of the 103-page complaint are heavily redacted, but the thrust of Amazon's complaint is that Amazon Web Services (AWS) was technically superior, that Microsoft's Azure cloud services failed key tests for the contract and that President Donald J. Trump steered the contract away from AWS.
The opening paragraphs get right to the heart of Amazon's argument:
A PDF of the redacted version of the filing via the Washington Post is available here.
Posted by Scott Bekker on December 10, 20190 comments
Sticker shock is one of the main customer objections to signing up for Microsoft Azure services. The flexibility of the cloud service makes Azure highly scalable but can lead to highly, er, scalable bills, as well.
While Microsoft has been pushing partners hard to sell Azure services to their customers for years, the company is finally also beginning to deliver the specialized tools that partners need to manage those costs across and on behalf of their customers.
In the last few weeks, Microsoft announced the general availability (GA) of Azure Cost Management for partners.
"With this update, partners and their customers can take advantage of Azure Cost Management tools available to manage cloud spend, similar to the cost management capabilities available for pay-as-you-go (PAYG) and enterprise customers today," wrote Aparna Gopalakrishnan, senior program manager for Azure Cost Management at Microsoft, in the blog post announcing GA of the tool.
One caveat of the initial version of the tool is that it is only available for cloud solution providers (CSPs) who have onboarded customers to the new Microsoft Customer Agreement. That agreement, a direct arrangement between Microsoft and the customer, largely sidelines partners in a manner that runs counter to the spirit of CSP, which was originally positioned as a program that allowed partners to control the billing relationship with their customers.
That said, there are still opportunities for partners to supplement customer needs and offer managed services around the Microsoft Customer Agreement, and Azure Cost Management could represent just such an opportunity. It provides a classic example of a partner being able to leverage expertise across dozens, hundreds or thousands of customers to optimize a customer's spending on Azure services and help make the bills predictable.
What the first version of Azure Cost Management provides is tools that allow partners to view, manage and analyze all of their customers' billing through a single pane of glass. Partners will be able to view and analyze costs by customer, subscription, resource group, resource, meter, service and other dimensions.
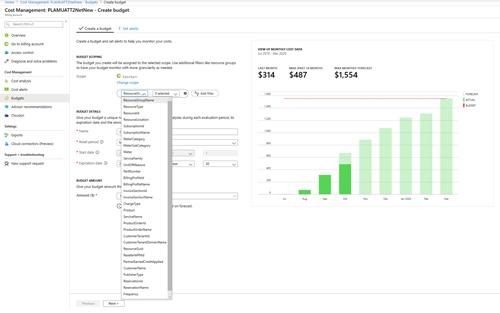 [Click on image for larger view.] One of the key capabilities of the partner-focused Azure Cost Management tool is the ability to set budgets and create alerts. (Source: Microsoft)
[Click on image for larger view.] One of the key capabilities of the partner-focused Azure Cost Management tool is the ability to set budgets and create alerts. (Source: Microsoft)
They can also track Partner Earned Credit (PEC) and, critically, set up notifications and automation using programmatic budgets. The tool also lets the partner enable the Azure Resource Manager policy that allows customers to access Cost Management data. Microsoft is making all of the functionality of the native tool available as REST APIs for automating the capabilities.
Microsoft committed to periodic updates of the tool. Among the first updates will be support for exporting data from the tool. The roadmap also calls for cost recommendations, optimization suggestions and showback features that allow partners to charge a markup on consumption costs.
Microsoft also plans to undo the main caveat by launching Azure Cost Management at retail rates for customers who are supported by a CSP partner but who are not on the Microsoft Customer Agreement.
Posted by Scott Bekker on December 03, 20190 comments