PRISM and Microsoft: What We Know So Far
It's way too early to draw conclusions about PRISM, the supposed, wide-ranging U.S. National Security Agency data collection program revealed by Edward Snowden that allegedly operates with the cooperation of major technology companies, including Microsoft. (The companies, including Microsoft, publicly and vigorously deny having voluntary or knowingly participated.)
With secret government programs, the details, and even the major structural elements, often don't come to light for decades. No matter what Microsoft partners feel about the legitimacy of the program or the reliability of the facts so far, it's hard to see the existence of the rumors about a secret U.S. government backdoor to customers' data as anything other than a stumbling block for trust in public cloud computing. The idea that the big public cloud vendors might have standing agreements with the U.S. government to share customer data runs counter to the spirit, if not the legalistic language, of any privacy policy.
Here's a brief primer on PRISM elements of interest to Microsoft partners:
PRISM
PRISM is a wide-ranging U.S. National Security Agency data collection program aimed at tracking terrorists and revealed earlier this month by former Booz Allen Hamilton contractor Edward Snowden via the Washington Post and the Guardian. Unveiled simultaneously with revelations about NSA access to information about call logs through the major telecoms, PRISM more directly affects the public cloud. According to the Post's article:
"The National Security Agency and the FBI are tapping directly into the central servers of nine leading U.S. Internet companies, extracting audio and video chats, photographs, e-mails, documents, and connection logs that enable analysts to track foreign targets, according to a top-secret document obtained by The Washington Post."
The Guardian, meanwhile, reported that Britain's equivalent of NSA, called GCHQ, is also able to tap into the servers of the nine organizations.
Special Source Operations
In one of the most explosive elements of the story for the IT industry, NSA has a special seal, or logo, for the companies whose servers are accessed. It's called "Special Source Operations," and the Post's annotation of the leaked four-slide NSA deck defines SSO as, "The NSA term for alliances with trusted U.S. companies."
Microsoft's Special Position
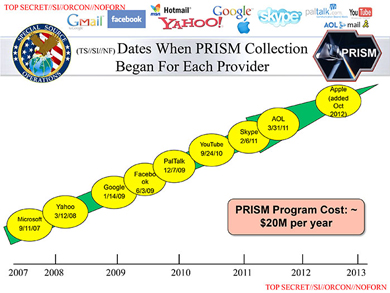
While the SSO badge isn't good for any of the companies' privacy credentials and Google seems the most alarmed about damage to its reputation, Microsoft has more explaining to do than the others. According to a slide in the leaked NSA deck titled, "Dates When PRISM Collection Began For Each Provider," Microsoft was the first partner recruited. According to the slide, Microsoft came aboard Sept. 11, 2007. Yahoo appears next in March 2008, followed by Google in January 2009, Facebook in June 2009, PalTalk in December 2009, YouTube in September 2010, Skype in February 2011 (before the Microsoft acquisition), AOL in March 2011 and Apple in October 2012.
 Source: Washington Post
Source: Washington Post
Companies Push Back
Understandably, the Internet companies have been pushing back aggressively. Microsoft was out immediately with a denial:
"We provide customer data only when we receive a legally binding order or subpoena to do so, and never on a voluntary basis. In addition we only ever comply with orders for requests about specific accounts or identifiers. If the government has a broader voluntary national security program to gather customer data we don't participate in it."
Other companies made similar statements, and Google went further, writing an open letter to U.S. Attorney General Eric Holder and FBI Director Robert Mueller on June 11 pressing for permission to make public how many government requests it gets.
In the wake of that letter, Microsoft last week revealed how many requests it has gotten from federal, state and local governments -- between 6,000 and 7,000 requests affecting as many as 32,000 accounts.
Meanwhile, Google continues to push back the hardest of any of the companies on the story. David Drummond, senior vice president and chief legal officer at Google, participated in a Web chat Q&A at the Guardian on Wednesday.
In response to one question, Drummond wrote:
"I'm not sure I can say this more clearly: we're not in cahoots with the NSA and theirs is [sic] no government program that Google participates in that allows the kind of access that the media originally reported. Note that I say 'originally' because you'll see that many of those original sources corrected their articles after it became clear that the PRISM slides were not accurate. Now, what does happen is that we get specific requests from the government for user data. We review each of those requests and push back when the request is overly broad or doesn't follow the correct process. There is no free-for-all, no direct access, no indirect access, no back door, no drop box."
Project Chess
This week, The New York Times added a new code name to the privacy/secrecy stew with some reporting on a Skype program predating the Microsoft acquisition, called "Project Chess." As the Times explains it, based on anonymous sources, Skype began Project Chess as a secret program "to explore the legal and technical issues in making Skype calls readily available to intelligence agencies and law enforcement officials."
The Times added: "Microsoft executives are no longer willing to affirm statements, made by Skype several years ago, that Skype calls could not be wiretapped. Frank X. Shaw, a Microsoft spokesman, declined to comment."
Posted by Scott Bekker on June 20, 2013